HUMAN's Satori Threat Intelligence and Research Team this week released a report detailing a significant ad fraud operation dubbed Camu. This Brazil-based scheme, which peaked at 2.5 billion daily bid requests across 132 domains, exploits pirated content websites to generate fraudulent ad revenue. The operation, uncovered in December 2023, employs sophisticated domain cloaking techniques to evade detection by advertisers and ad networks.
This case highlights the ongoing cat-and-mouse game between ad fraud perpetrators and cybersecurity researchers.
Camu, derived from the Brazilian Portuguese word for cloaking, represents the largest cloaking operation identified by HUMAN's Satori team to date. The scheme's scale is staggering, with its peak daily bid request volume comparable to the entire daily ad activity of major U.S. cities like Atlanta or Sacramento.
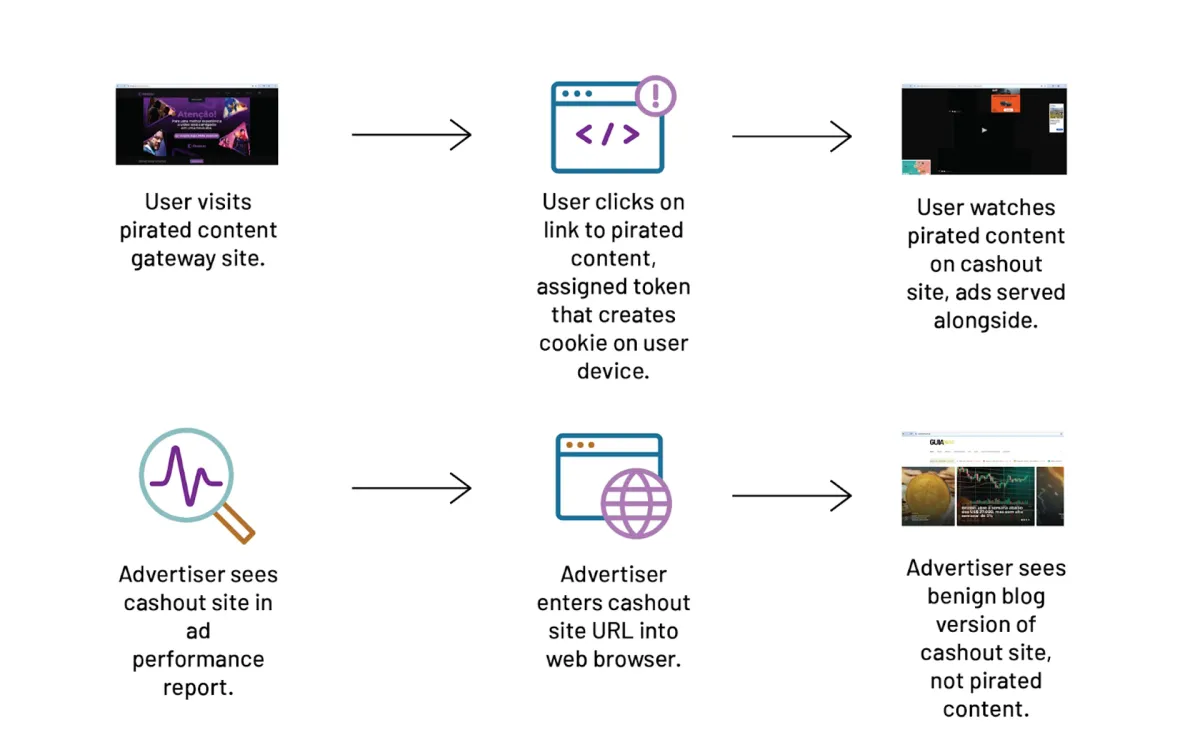
According to the report, Camu operates through a two-pronged approach:
- Pirated Content Gateways: Users access websites listing available pirated movies and TV shows.
- Cashout Sites: Clicking on content redirects users to secondary domains displaying both pirated material and multiple programmatic ads.
The crux of Camu's deception lies in its domain cloaking mechanism. When visited directly, these cashout sites present benign, blog-like content that wouldn't raise red flags for advertisers. However, users arriving via the pirated content gateways are shown the actual pirated material surrounded by ads.
This cloaking is achieved through a complex redirection process:
- Users clicking on content from the gateway site are assigned a token.
- This token installs a cookie on the user's browser, typically set to expire after 30 minutes.
- The presence of this cookie determines which version of the cashout site is displayed - pirated content or benign blog.
The Satori team notes that Camu goes beyond simple referral deletion. Some cashout domains actively add false referral information, making it appear as though traffic originated from organic searches or reputable sites rather than piracy gateways.
An alternative cashout mechanism was also observed, where instead of redirecting to distinct domains, Camu sites may trigger pop-ups linking to malicious phishing sites or drive-by malware downloaders. These referrals often generate additional revenue for the site owners.
The impact of Camu on the digital advertising ecosystem is significant. Even meticulous review of delivery confirmation or audit reports may not reveal the true nature of ad placements, as the cloaking mechanism effectively conceals the association with pirated content.
Since HUMAN deployed mitigations over the past nine months, the volume of bid requests on Camu-associated domains has decreased substantially, from 2.5 billion to approximately 100 million per day. However, the operation remains active, highlighting the persistent nature of such fraud schemes.
The Camu investigation underscores several key challenges in combating ad fraud:
- Sophisticated Cloaking: The use of cookies and complex redirection paths makes it difficult to consistently reproduce fraudulent behavior in controlled environments.
- Referral Obfuscation: By manipulating referral data, Camu obscures the relationship between piracy gateways and cashout domains.
- Scale of Operation: With billions of daily bid requests at its peak, Camu demonstrates the potential for massive financial impact on advertisers and legitimate publishers.
- Adaptability: The presence of alternative cashout mechanisms shows the operators' ability to diversify their fraudulent activities.
HUMAN's report emphasizes the importance of active defensive measures beyond standard report reviews. The company states that its Advertising Protection service is capable of identifying unexpected behaviors like those exhibited by Camu and filtering traffic to prevent fraudulent payouts.
The Satori team has published a list of 132 domains associated with the Camu operation. Researchers continue to monitor and capture new domains added to the network.
Key facts from the Camu investigation
- Peak daily bid requests: 2.5 billion
- Number of domains involved: 132
- Discovery date: December 2023
- Current daily bid requests: Approximately 100 million
- Primary location of operation: Brazil
- Cloaking method: Cookie-based content switching
- Alternative cashout method: Malicious pop-up ads

