Oracle this month exposed an ad fraud operation in Connected TV, spoofing more than 28.8 million U.S. valid household IP addresses, including approximately 3,600 apps and 3,400 unique CTV device models. Oracle named the ad fraud operation as StreamScam.
According to Oracle, StreamScam exploits flaws in CTV ad serving technology to fool advertisers into paying for ads that were never delivered to households. A previous CTV ad fraud operation, ICEBUCKET involved two million spoofed household IP addresses, 300 app IDs, and 1,000 CTV device IDs.
Oracle says the usage of valid household IP addresses demonstrates the sophistication of StreamScam compared to previous CTV ad fraud operations.
AdAdge reports StreamScam led to $14.5 million in misspent advertising
StreamScam perpetrators capitalized on vulnerabilities in the technology Server-Side Ad Insertion (SSAI), the technology combines content and ads into a single video stream that can play seamlessly with no delays on end-user devices, such as Roku, AppleTV, and FireTV.
Using Moat technology, Oracle discovered that the StreamScam perpetrators built a network of servers that sent ad impression events to Moat and advertisers without actually sending ad and video content to users. Oracle says the fraudsters forged household IP addresses, app IDs, and device IDs in the measurement events to make it appear that ads had played in those environments when in fact they did not.
“Where advertising dollars go, criminals will follow, and rapidly-growing channels like CTV are presenting new opportunities for ad fraud and theft,” said Mark Kopera, head of product for Oracle Moat. “In a quickly evolving landscape of risks and opportunities, it’s critical for marketers to work with trusted partners that have the knowledge, experience, and scale to identify and block new threats as they emerge. We look forward to working with companies across the digital advertising ecosystem to expose and work to prevent this and other emerging types of ad fraud, as well as protect advertisers’ vital campaign resources.”
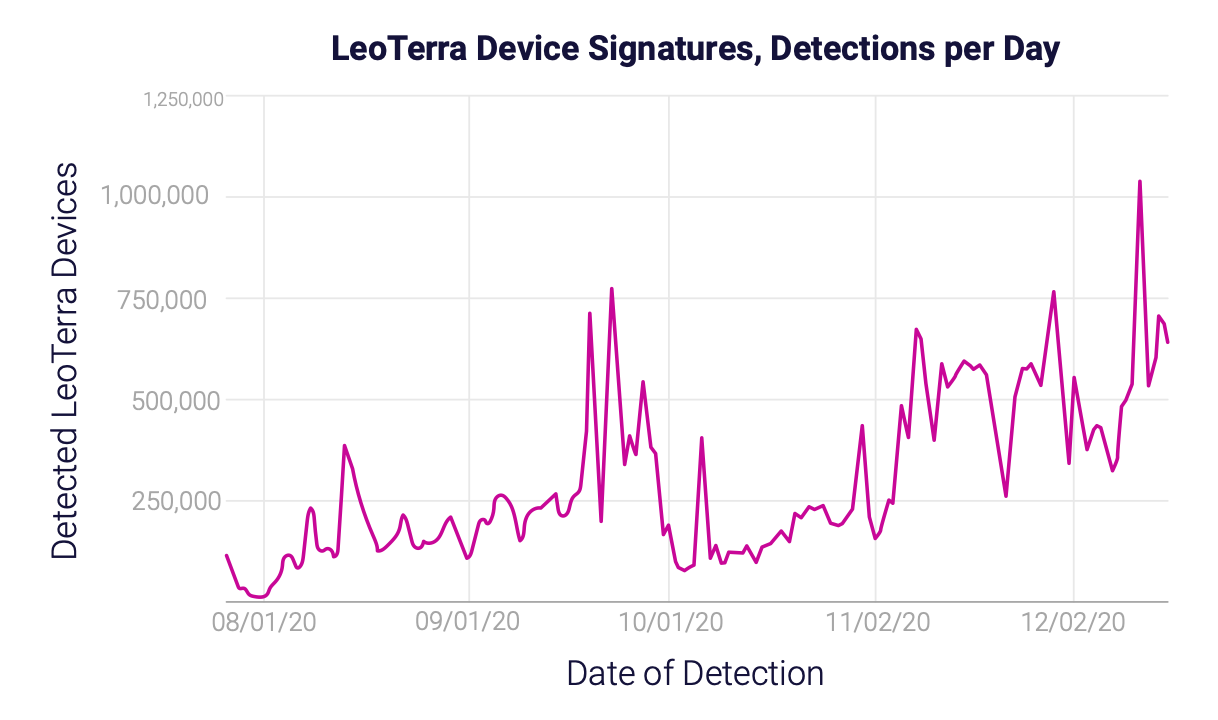
DoubleVerify, a competitor of Oracle Moat, commented that it has detected the StreamScam SSAI scheme back in July 2020. DoubleVerify says it has labeled this scheme LeoTerra and began blocking it and alerting the impacted clients.
DoubleVerify tracked 44M unique device signatures spoofed by LeoTerra/ StreamScam ad fraud operation, and 4,700 spoofed apps.
DoubleVerify explains how SSAI ad fraud operations run:
- Fraudsters gather the details of legitimate users (i.e. the IP addresses or app bundleIDs).
- Fraudsters copy these details to mask their activity from being detected.
- Fraudsters use the spoofed details of legitimate users to send fraudulent ad requests into the ecosystem.

