On June 27, 2024, Google and Mozilla announced their decisions to stop trusting Entrust's public TLS certificates issued after specific dates in late 2024. This move comes in response to concerns about Entrust's ability to meet the CA/Browser Forum's requirements for a publicly trusted certificate authority (CA).
According to the Chrome Root Program and Chrome Security Team, Google will cease trusting TLS server authentication certificates validating to Entrust roots with the earliest Signed Certificate Timestamp (SCT) dated after November 11, 2024 (11:59:59 PM UTC). This change will take effect in Chrome 131 and higher versions across Windows, macOS, ChromeOS, Android, and Linux platforms.
Mozilla, as stated by Ben Wilson on July 31, 2024, will implement a distrust-after date for TLS certificates issued after November 30, 2024, for several Entrust root CAs.
The decision affects the following Entrust root certificates:
- Entrust Root Certification Authority - EC1
- Entrust Root Certification Authority - G2
- Entrust.net Certification Authority (2048)
- Entrust Root Certification Authority
- Entrust Root Certification Authority - G4
- AffirmTrust Commercial
- AffirmTrust Networking
- AffirmTrust Premium
- AffirmTrust Premium ECC
Google cited a "pattern of compliance failures" over the past six years as the primary reason for their decision. The Chrome Security Team expressed that Entrust's actions have "eroded confidence in their competence, reliability, and integrity as a publicly-trusted CA Owner."
Mozilla echoed similar concerns, stating that Entrust's proposed plan to address recent incidents was insufficient to restore trust in their operations. The browser developer emphasized the need for "a candid and clear accounting of failures and their root causes, a detailed and credible plan for how they can be addressed, and concrete commitments based on objective and externally measurable criteria."
The impact of this decision on website operators and users is significant. Website operators using Entrust certificates will need to transition to a new publicly-trusted CA as soon as possible to avoid disruptions. Users of Chrome and Mozilla browsers accessing websites with affected Entrust certificates issued after the specified dates will see full-page interstitial warnings, indicating an insecure connection.
To help website operators determine if they are affected, Google recommends using the Chrome Certificate Viewer. Operators can check if the "Organization (O)" field listed beneath the "Issued By" heading contains "Entrust" or "AffirmTrust." If so, action is required to replace the certificate before the distrust dates.
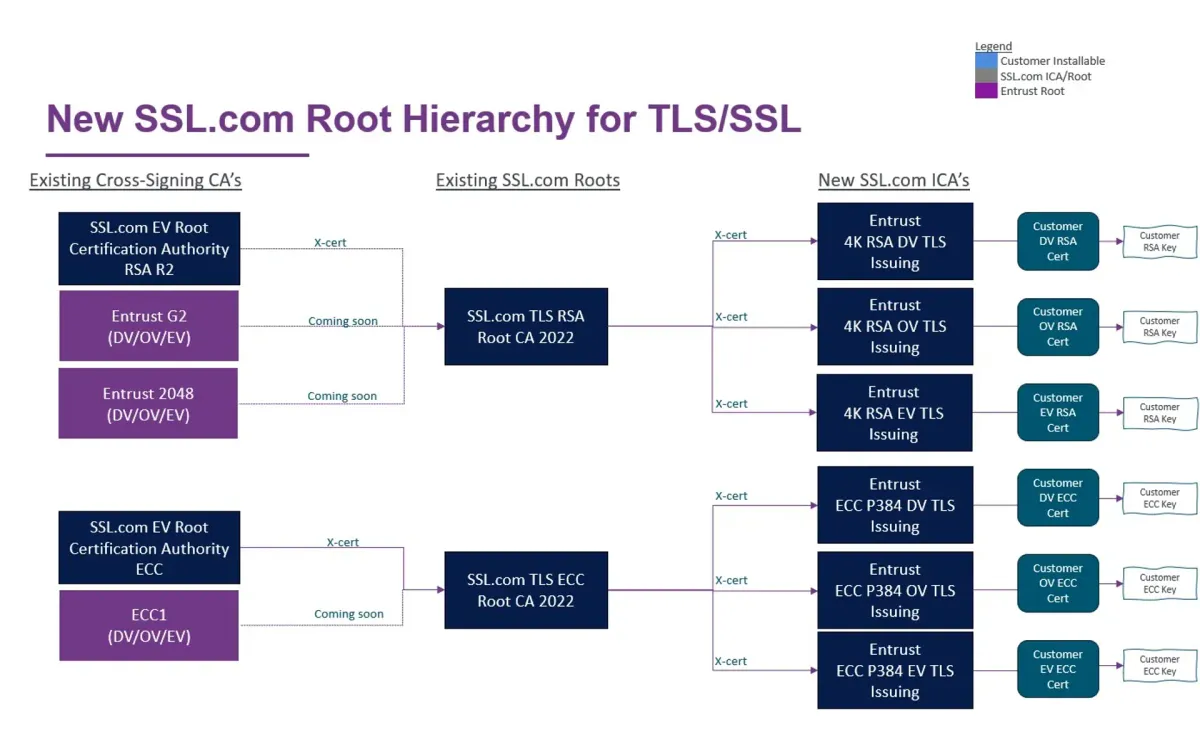
In response to these developments, Entrust has announced a partnership with SSL.com, a publicly trusted CA. Under this arrangement, SSL.com will act as Entrust's External Registration Authority (RA), performing pre-issuance vetting of certificate applicants. SSL.com will be responsible for domain validation, certificate issuance, and revocation, as well as handling any incidents that may occur.
Cloudflare, a major internet infrastructure company, has responded to the situation by adding SSL.com as a certificate authority option for its customers. This allows Cloudflare users currently relying on Entrust to transition to SSL.com certificates seamlessly. Cloudflare will handle all issuances and renewals automatically, simplifying the certificate management process for affected customers.
For enterprise users, both Google and Mozilla have provided options to mitigate the impact of this change. Chrome users or enterprises can explicitly trust the affected certificates on platforms and versions of Chrome relying on the Chrome Root Store. This can be done through methods such as Group Policy Objects on Windows. Starting with Chrome 127, enterprises can override Chrome Root Store constraints by installing the corresponding root CA certificate as a locally-trusted root on the platform Chrome is running.
Mozilla supports the arrangement between Entrust and SSL.com, recognizing that SSL.com, as the operator of the root CA within Mozilla's root CA program, will ultimately be responsible for any incidents that may occur.
To help website operators and developers test these changes before they take effect, Google has added a command-line flag in Chrome 128 that allows administrators and power users to simulate the effect of an SCTNotAfter distrust constraint.
The tech giants emphasize that this decision is not taken lightly and is aimed at preserving the integrity of the Web PKI ecosystem. They hope that Entrust will work to address the root causes of these incidents and eventually re-establish confidence in its internal policies, processes, tooling, and technology, as well as its commitment to the Web PKI community.
Key facts and dates
- Google Chrome distrust date: November 11, 2024 (11:59:59 PM UTC)
- Mozilla Firefox distrust date: November 30, 2024
- Affected browsers: Chrome 131 and higher (Windows, macOS, ChromeOS, Android, Linux), Firefox (all platforms)
- Number of affected Entrust root certificates: 9
- Entrust's partnership announcement: SSL.com to act as External Registration Authority
- Cloudflare's response: Addition of SSL.com as a certificate authority option
Website operators and enterprise IT administrators are advised to review their SSL/TLS certificate deployments and plan for migration to alternative certificate authorities well before the distrust dates to ensure uninterrupted secure connections for their users.

