Three days after its announcement on January 30, 2025, the World Wide Web Consortium (W3C) has taken a significant step forward in digital identity verification by introducing the Controlled Identifiers (CIDs) v1.0 specification. This new standard aims to establish a robust framework for cryptographic verification and secure digital interactions.
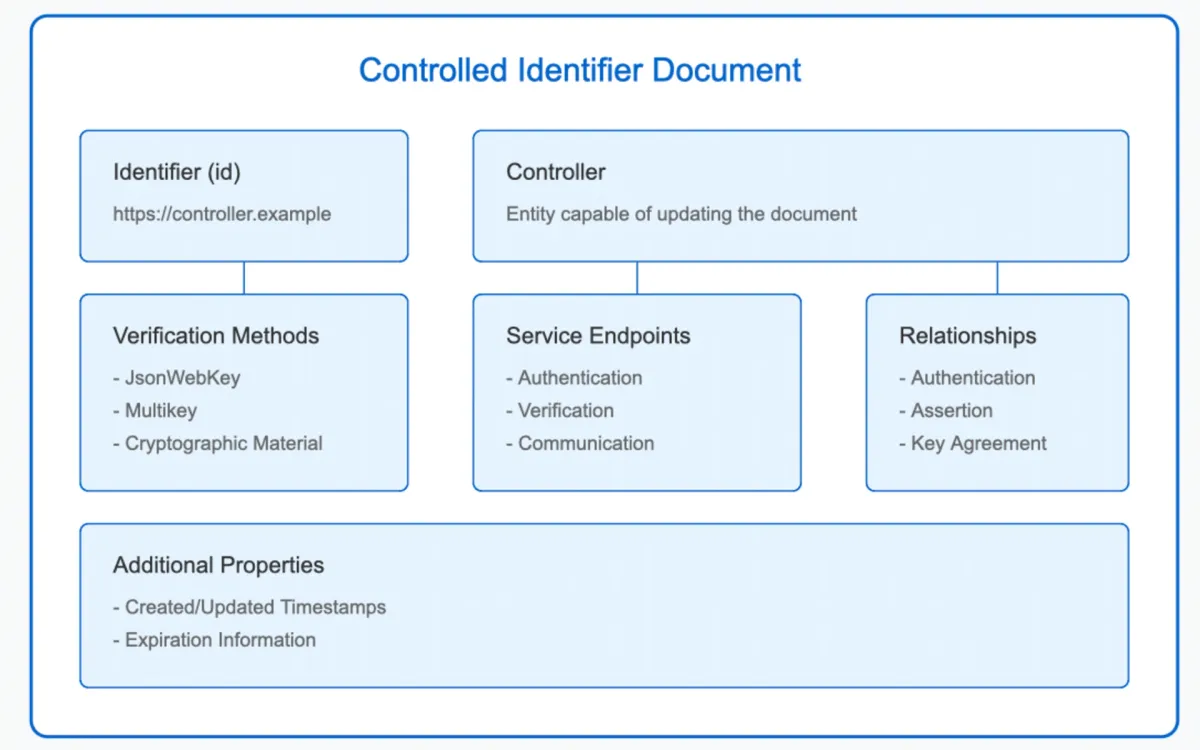
According to the W3C Verifiable Credentials Working Group, a controlled identifier document serves as a comprehensive technical foundation that contains cryptographic material and defines service endpoints. These components enable the verification of cryptographic proofs and facilitate interactions with the identifier's controller.
The technical implementation builds upon established cryptographic principles. A controlled identifier document specifies verification relationships between an identifier and multiple verification methods. The document structure supports various cryptographic mechanisms, including authentication keys, assertion methods, and capability delegation protocols.
In terms of security features, the specification introduces multiple verification relationships. These include authentication for proving identity, assertion methods for making claims, and key agreement protocols for encrypted communications. The framework also supports capability invocation and delegation mechanisms, providing granular control over digital authorizations.
The specification defines strict requirements for conformance. A controlled identifier document must contain specific properties, including a unique identifier and optional controller information. The document structure supports both embedded and referenced verification methods, allowing for flexible implementation approaches.
Cryptographic material in the specification can be expressed using two standardized formats: JsonWebKey and Multikey. The JsonWebKey format follows the JSON Web Key specification RFC7517, while Multikey introduces a compact binary encoding scheme for various key types including ECDSA, Ed25519, and BLS12-381.
For implementation purposes, the specification provides detailed algorithms for base encoding and decoding operations. These algorithms ensure consistent handling of cryptographic material across different systems. The specification also defines clear error handling procedures for various failure scenarios.
Privacy considerations form a central aspect of the standard. The specification strongly advises against including personal data in controlled identifier documents, particularly for non-public entities. It recommends using pairwise identifiers for different relationships to prevent unwanted correlation.
The Working Group has established specific criteria for transitioning the specification from its current Candidate Recommendation phase. Implementation feedback will be collected until February 28, 2025. The group requires at least two independent implementations for each mandatory feature before advancing to the Proposed Recommendation stage.
Service providers implementing the specification must adhere to strict security protocols. The standard includes comprehensive guidance on key management, verification method rotation, and revocation procedures. These security measures aim to protect against various threat vectors while maintaining system flexibility.
Technical implementers must follow specific data handling requirements. The specification mandates the use of URL-conformant identifiers and requires proper formatting of verification methods. Service endpoints must be properly structured and include required properties such as type and service endpoint information.
The implementation timeline extends through the coming months. According to the Working Group's documentation, the specification will not advance to Proposed Recommendation before February 28, 2025, allowing time for thorough testing and feedback from early implementers.
W3C maintains a public list of patent disclosures related to the specification, ensuring transparency in intellectual property matters. The specification operates under the W3C Patent Policy, with all implementations subject to royalty-free licensing requirements.
Organizations interested in implementing the specification can access detailed technical documentation through the W3C's official channels. Implementation reports will be collected and analyzed to assess the specification's practical viability and interoperability characteristics.
For technical conformance, implementations must handle various data formats and protocols. These include JSON-LD contexts, Multibase encodings, and multiple cryptographic key formats. The specification provides detailed algorithms and test vectors to ensure consistent implementation across different platforms.
The standard represents a significant advancement in digital identity infrastructure, building upon previous work in decentralized identifiers and verifiable credentials. Its development incorporates extensive feedback from the technical community and addresses real-world implementation challenges in digital identity management.

