
On October 2, 2024, Cloudflare, a leading internet security company, announced that it had successfully defended against the largest cyber attack in internet history. This massive attack, known as a Distributed Denial of Service (DDoS) attack, peaked at an unprecedented 3.8 terabits per second (Tbps). For comparison, this is equivalent to streaming over 3.8 million high-definition movies simultaneously.
What is a DDoS attack?
A DDoS attack is like a virtual traffic jam. Imagine thousands of cars suddenly flooding a highway, preventing regular drivers from reaching their destinations. In the digital world, attackers use networks of compromised computers to flood a website or online service with so much traffic that it becomes overwhelmed and crashes, denying access to legitimate users.
Record-breaking attack details
The attack campaign began in early September 2024 and lasted for about a month. During this period, Cloudflare's systems fought off over a hundred extremely large attacks. Many of these attacks exceeded 2 billion packets per second (Bpps) and 3 terabits per second (Tbps).
According to Cloudflare, the largest single attack reached an astounding 3.8 Tbps, making it the biggest DDoS attack ever publicly disclosed. This record-breaking attack lasted for 65 seconds before being automatically mitigated by Cloudflare's defense systems.
Who was targeted?
Cloudflare reported that the attacks targeted multiple customers across various industries, including:
- Financial services
- Internet companies
- Telecommunications providers
The company did not disclose specific names of the targeted organizations to protect their privacy.
Where did the attacks come from?
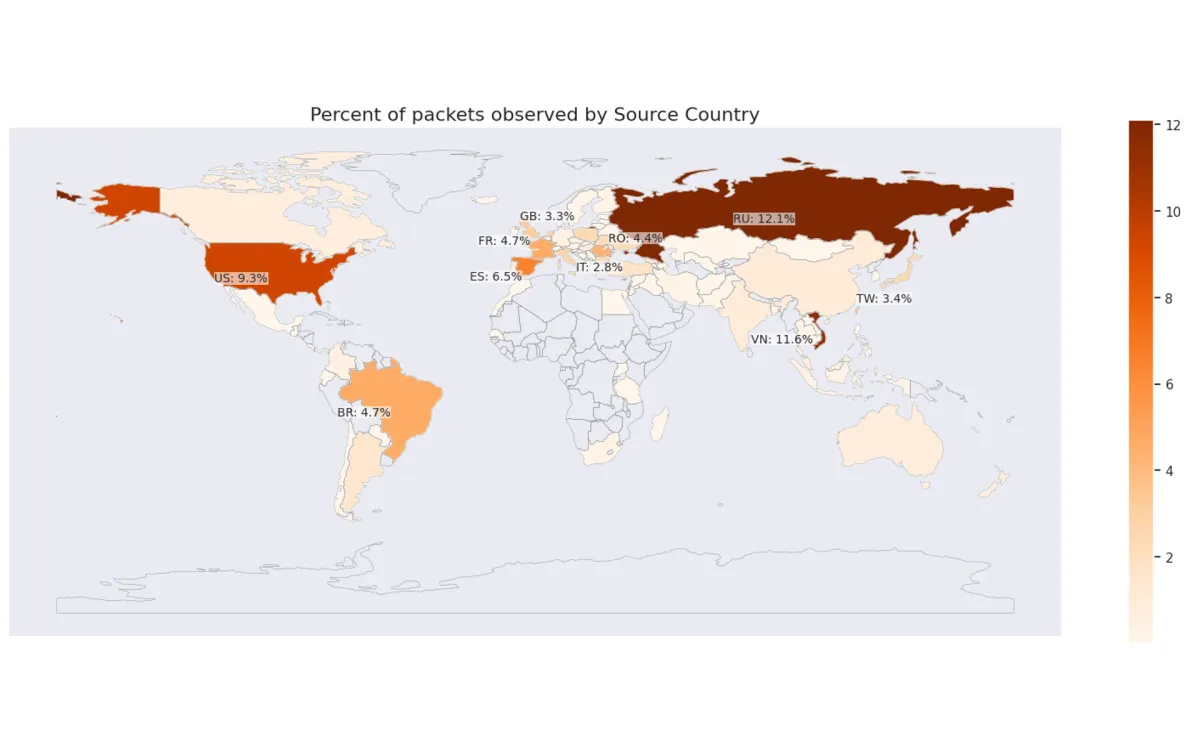
The attacks originated from various locations around the world. However, Cloudflare noted that larger portions of the attack traffic came from:
- Vietnam
- Russia
- Brazil
- Spain
- United States
The attackers used different types of compromised devices to launch their assault, including:
- MikroTik devices (networking equipment)
- DVRs (digital video recorders)
- Web servers
- ASUS home routers
How did Cloudflare stop the attacks?
Cloudflare's defense against these massive attacks relied on several key factors:
- Global Network: Cloudflare uses a technique called "anycast" to spread incoming traffic across its worldwide network of data centers. This helps distribute the impact of an attack, making it more manageable.
- Automated Detection: The company's systems can automatically identify attack patterns and create "fingerprints" to block malicious traffic.
- Efficient Packet Processing: Cloudflare uses advanced technology to inspect and discard malicious packets very quickly, without consuming too much computing power.
- Constant Vigilance: The defense systems run continuously across Cloudflare's entire network, allowing for rapid response to emerging threats.
Why this matters
These record-breaking attacks highlight the ever-growing scale of cyber threats facing businesses and organizations online. As our reliance on internet services continues to increase, the potential impact of such attacks becomes more severe.
Cloudflare's ability to mitigate these attacks automatically and without disruption to its customers demonstrates the importance of robust, scalable cybersecurity solutions in maintaining the stability and reliability of the internet.
Key Facts
- Largest DDoS attack ever publicly disclosed: 3.8 Tbps
- Attack campaign duration: Approximately one month (early September to early October 2024)
- Number of large-scale attacks mitigated: Over 100
- Industries targeted: Financial services, Internet, Telecommunications, and others
- Main countries of origin: Vietnam, Russia, Brazil, Spain, United States
- Types of compromised devices used: MikroTik devices, DVRs, Web servers, ASUS home routers

