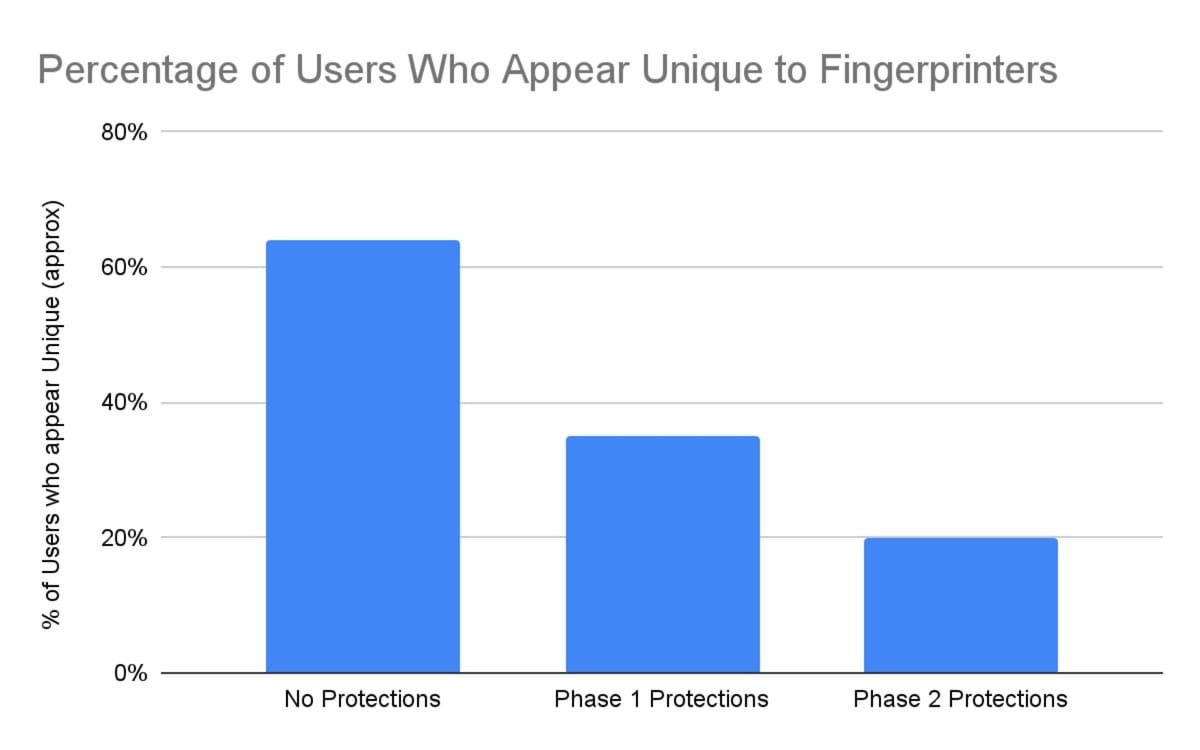
Mozilla announced the completion of the second phase of fingerprinting defenses in Firefox 145, marking a significant advancement in browser privacy protections that targets tracking techniques capable of following users across websites even when cookies are blocked. The announcement came through a blog post by Tom Ritter, detailing protections that cut the percentage of users identifiable through fingerprinting by nearly half.
Browser fingerprinting creates digital identifiers by collecting subtle details about device configurations, ranging from time zones to operating system settings, that collectively create unique profiles identifiable across different websites and browser sessions. Unlike cookies that users can delete, fingerprints persist across browsing sessions and work even in private browsing modes.
The new protections build on Firefox's Enhanced Tracking Protection framework, which has blocked known trackers since 2020. The latest phase specifically targets fingerprinting scripts that operate outside known tracker lists, addressing a broader spectrum of privacy threats than previous implementations.
Sign up for the free weekly newsletter
Your go-to source for digital marketing news.
No spam. Unsubscribe anytime.
Understanding browser fingerprinting
Browser fingerprinting represents a tracking methodology fundamentally different from cookies. While cookies store identifiers that users can view, delete, or block through browser settings, fingerprinting extracts inherent characteristics from browser and device configurations to create unique identification profiles.
The technique works by collecting dozens of data points about how browsers render content, which fonts systems have installed, how graphics hardware processes images, and numerous other configuration details. Each individual attribute might seem innocuous—time zone settings, screen resolution, installed plugins—but their combination creates patterns statistically unique to specific devices.
According to Mozilla's documentation, fingerprinting operates invisibly without user awareness or consent. Websites can query browser capabilities through standard application programming interfaces designed for legitimate functionality. A website checking graphics capabilities to optimize video playback uses the same APIs that fingerprinters employ to identify unique rendering characteristics.
The persistence of fingerprints creates particular privacy concerns. Users who clear cookies, switch to private browsing modes, or employ privacy tools still carry identical fingerprints because the underlying device and software configurations remain unchanged. Fingerprinting techniques can track users across months of browsing activity, surviving actions that would eliminate cookie-based tracking.
Mathematical analysis demonstrates why fingerprinting proves so effective. With enough data points, the probability of two users sharing identical fingerprints approaches zero. Research has shown that combinations of just 30-40 attributes can uniquely identify the majority of web users. Adding more sophisticated techniques like canvas fingerprinting, which analyzes pixel-level differences in how graphics cards render identical images, increases uniqueness further.
The advertising industry has increasingly adopted fingerprinting as browsers restrict cookie usage. While less reliable than cookies for individual user identification, fingerprinting provides tracking capabilities that users cannot easily disable. This asymmetry between tracking power and user control motivated Mozilla's development of comprehensive defenses.
Firefox's Enhanced Tracking Protection relies on a list of known trackers provided by Disconnect. By default, Firefox blocks social media trackers, cross-site tracking cookies, fingerprinters, cryptominers, and tracking content. Total Cookie Protection, enabled by default in Standard mode, confines every cookie to the website where it was created, preventing cookies from tracking users across sites.
Technical implementation and methodology
Mozilla developed the fingerprinting defenses using global analysis of how browsers can be fingerprinted in real-world scenarios, according to the announcement. Firefox becomes the first browser with this level of insight into fingerprinting techniques and deployed defenses specifically designed to reduce trackability rather than simply blocking known trackers.
The protections operate on multiple layers. Enhanced Tracking Protection continues blocking known tracking and fingerprinting scripts from identified sources. Beyond script blocking, Firefox limits information available to websites through privacy-by-design approaches that preemptively shrink digital fingerprints.
Browsers provide application programming interfaces that allow websites to request information enabling legitimate features. Graphics hardware information, for example, allows websites to optimize games for specific computers. Trackers can request identical information solely to build fingerprints for cross-site tracking purposes.
Firefox has incrementally advanced fingerprinting protections since 2021, according to the announcement. The first phase addressed the most pervasive fingerprinting techniques, including graphics card rendering behaviors, installed fonts, and mathematical calculation variations between devices. Recent releases tackled additional information leaks used by fingerprinters, strengthening font protections and preventing websites from accessing hardware details including processor core counts, touchscreen capabilities, and taskbar dimensions.
The complete list of detailed protections appears in Mozilla's technical documentation. Research conducted by Mozilla shows these improvements reduced the percentage of users appearing unique to fingerprinters by almost half.
Deployment strategy and user experience
The new fingerprinting protections debut in Private Browsing Mode and Enhanced Tracking Protection Strict mode initially, with plans to enable them by default across all browsing sessions. This phased deployment allows Mozilla to refine the protections before broader implementation.
Mozilla designed the protections to balance disruption of fingerprinting with maintenance of web usability. More aggressive blocking would break legitimate website features, according to the announcement. Calendar, scheduling, and conferencing tools legitimately require accurate time zone information. Firefox's approach targets the most significant fingerprinting vectors while preserving functionality needed by many websites to operate normally.
The layered defense system significantly reduces tracking without degrading browsing experiences, according to the announcement. Mozilla provides detailed documentation about specific behaviors and instructions for recognizing website problems caused by the protections. Users can disable protections for individual sites while maintaining overall privacy protections, ensuring control over browsing experience.
Industry context and competitive landscape
The announcement arrives amid intensifying browser privacy competition and regulatory pressure on tracking practices. Google announced plans to lift fingerprinting restrictions for advertisers in February 2025, prompting criticism from the UK Information Commissioner's Office, which labeled the decision "irresponsible." Google's policy shift permits device fingerprinting particularly for Connected TV advertising starting February 16, 2025, creating divergent approaches between major browser vendors.
Apple's Safari has implemented Advanced Fingerprinting Protection, which becomes default for all browsing sessions in Safari 26, launching September 2025. Safari targets known fingerprinting scripts rather than legitimate analytics implementations, according to release notes published September 3, 2025.
Chrome introduced IP Protection features for Incognito mode, with implementation beginning May 2025. The technology employs a two-hop proxy system to prevent third-party tracking while maintaining critical services like fraud prevention.
The varying approaches across browsers reflect fundamental tensions between user privacy protections and advertising industry requirements. Google faced backlash from privacy advocates when urging business owners to oppose California Assembly Bill 566, which would require browsers to offer built-in opt-out settings for data collection.
Buy ads on PPC Land. PPC Land has standard and native ad formats via major DSPs and ad platforms like Google Ads. Via an auction CPM, you can reach industry professionals.
Impact on marketing measurement
Fingerprinting restrictions create measurement challenges for digital advertisers who rely on cross-site tracking for attribution and campaign optimization. Unlike cookies that provide explicit user consent mechanisms through browser settings and consent management platforms, fingerprinting relies on signals users cannot easily eliminate.
Even when users select "clear all site data" in browsers, organizations employing fingerprinting techniques can immediately re-identify devices, according to the UK Information Commissioner's Office statement on Google's fingerprinting policy changes. This persistence makes fingerprinting particularly concerning from privacy perspectives but valuable for advertisers seeking consistent measurement.
The ICO highlighted that organizations implementing fingerprinting techniques must demonstrate compliance with data protection requirements, including transparency, freely-given consent, fair processing, and information rights such as the right to erasure. Based on current understanding of fingerprinting techniques, this represents a high compliance threshold, according to the regulator's December 2024 statement.
Safari's Intelligent Tracking Prevention has progressively restricted cross-site tracking capabilities since 2017, forcing advertisers to develop alternative attribution methodologies. Each browser update tightens privacy controls while advertising platforms enhance modeling capabilities to maintain measurement effectiveness with reduced data availability.
Marketing teams increasingly rely on attribution modeling, incrementality testing, and survey-based measurement that operates independently of browser tracking limitations. Google Ads implemented modeled conversions to infer conversions when direct tracking information is unavailable, reflecting industry adaptation to privacy restrictions.
Technical architecture details
Firefox's fingerprinting protections target specific information categories that contribute to unique browser signatures. Canvas randomization prevents websites from using HTML5 canvas elements to generate unique fingerprints based on how graphics cards render images. Each device renders canvas elements slightly differently due to graphics hardware and driver variations, creating identifiable patterns.
Font enumeration protections limit website access to installed fonts, preventing fingerprinters from building profiles based on unique font combinations. Operating system, language settings, and software installations create distinctive font collections that contribute to fingerprint uniqueness.
Hardware information restrictions prevent websites from querying processor specifications, memory configurations, and peripheral device capabilities. The number of CPU cores, touchscreen support levels, and screen dimensions provide fingerprinting data points that collectively identify specific devices.
Script blocking targets known fingerprinting libraries and techniques identified through Mozilla's research. The blocking occurs at the network level for known trackers and through API restrictions for scripts attempting to access fingerprintable information.
According to Mozilla's documentation, the protections introduce controlled randomization for certain API responses, injecting noise into data returned by fingerprinting vectors. This approach prevents complete blocking of legitimate functionality while reducing fingerprint consistency across browsing sessions.
Privacy ecosystem developments
Mozilla's fingerprinting protections align with broader privacy initiatives across the web ecosystem. Total Cookie Protection, introduced in Firefox previously, compartmentalizes cookies to prevent cross-site tracking. The feature stores cookies in separate containers for each website, preventing third parties from correlating user activity across different domains.
Chrome's Privacy Sandbox initiative attempts to develop privacy-preserving alternatives to third-party cookies while maintaining advertising functionality. Stakeholders have expressed concerns that Privacy Sandbox APIs would replace internet data ingredients with Google's own products, potentially creating competitive advantages for Google's advertising systems.
The April 2025 announcement that Chrome would maintain third-party cookies while continuing Privacy Sandbox development created a dual-track approach, providing time for further refinement without disrupting the existing advertising ecosystem. Google's original plan to deprecate third-party cookies by early 2025 faced substantial criticism regarding competitive implications and technical readiness.
Regulatory enforcement of privacy requirements intensifies alongside technical protections. Google faced a €325 million fine for Gmail ads and cookie violations in September 2025, demonstrating financial risks of improper tracking implementation. German courts continue clarifying cookie banner requirements, maintaining regulatory focus on consent mechanism design.
Future privacy roadmap
Mozilla stated that Firefox remains committed to fighting for user privacy, allowing users to enjoy the web on their terms. The company encourages users to upgrade to the latest Firefox version to activate the fingerprinting protections automatically, requiring no additional extensions or configurations.
The phased deployment strategy suggests Mozilla will monitor compatibility issues and user feedback before enabling protections by default across all browsing sessions. Similar approaches have been used for Total Cookie Protection and other privacy features that initially launched in Private Browsing mode before broader rollout.
Industry observers anticipate continued browser competition on privacy features as user awareness of tracking practices grows. The divergent approaches between Firefox's restrictive fingerprinting protections, Chrome's Privacy Sandbox APIs, and Safari's Intelligent Tracking Prevention reflect different balances between privacy protection and web functionality preservation.
For marketing professionals, the fingerprinting restrictions create additional measurement challenges requiring diversified attribution strategies. Reliance on single tracking methods becomes increasingly risky as browser vendors implement varying privacy protections with different technical implementations and deployment timelines.
The advancement of privacy-enhancing technologies including confidential computing, trusted execution environments, and secure multi-party computation may provide paths for measurement that satisfy both privacy requirements and business needs. However, implementation complexity and standardization challenges remain significant obstacles to widespread adoption.
Subscribe PPC Land newsletter ✉️ for similar stories like this one
Timeline
- 2017: Safari introduces Intelligent Tracking Prevention, beginning progressive restriction of cross-site tracking capabilities
- 2020: Firefox launches Enhanced Tracking Protection, blocking known trackers and invasive practices
- 2021: Firefox begins incrementally enhancing anti-fingerprinting protections targeting common fingerprinting information
- January 2024: Chrome begins testing Tracking Protection with 1% of users globally
- July 2024: Safari unveils Private Browsing 2.0 with link tracking protection and advanced fingerprinting defenses
- December 2024: Google announces policy changes permitting fingerprinting for advertisers starting February 2025
- February 2025: Chrome introduces IP Protection masking IP addresses in Incognito mode
- May 2025: Google's Q1 Privacy Sandbox report documents stakeholder concerns about fingerprinting alternatives
- September 2025: Safari 26 activates Advanced Fingerprinting Protection by default for all browsing sessions
- November 2025: Firefox 145 completes second phase of fingerprinting defenses, reducing user trackability by half
Subscribe PPC Land newsletter ✉️ for similar stories like this one
Summary
Who: Mozilla, creator of Firefox browser, developed and deployed the enhanced fingerprinting protections. Tom Ritter announced the completion of the second phase through the Mozilla blog.
What: Firefox 145 introduces comprehensive anti-fingerprinting defenses that reduce the percentage of users identifiable through fingerprinting by nearly half. The protections include canvas randomization, font and hardware information restrictions, and script blocking targeting fingerprinting techniques. The system operates through layered defenses combining known tracker blocking with privacy-by-design approaches that limit information available to websites.
When: The announcement came in November 2025 with the release of Firefox 145. Firefox began incrementally advancing fingerprinting protections in 2021, with the first phase addressing the most pervasive techniques. The latest phase completes work targeting additional information leaks used by fingerprinters. The protections are currently available in Private Browsing Mode and Enhanced Tracking Protection Strict mode, with plans for broader default deployment.
Where: The protections operate within Firefox browser across all platforms where Firefox is available. The fingerprinting defenses work globally, affecting all websites that attempt to collect fingerprinting information from Firefox users. The protections are particularly relevant given browser fingerprinting operates across the entire web ecosystem, following users across different websites and services.
Why: Browser fingerprinting represents a pervasive tracking technique that identifies users even when cookies are blocked or users employ private browsing modes. Fingerprints persist for months across browser sessions, allowing tracking without user knowledge or consent. Mozilla developed the protections to advance its mission of building a healthier, transparent, and privacy-preserving web ecosystem. The defenses balance disruption of tracking with maintenance of web functionality, targeting the most significant fingerprinting vectors while preserving legitimate website features. The announcement reflects intensifying browser competition on privacy features and regulatory pressure on tracking practices.

