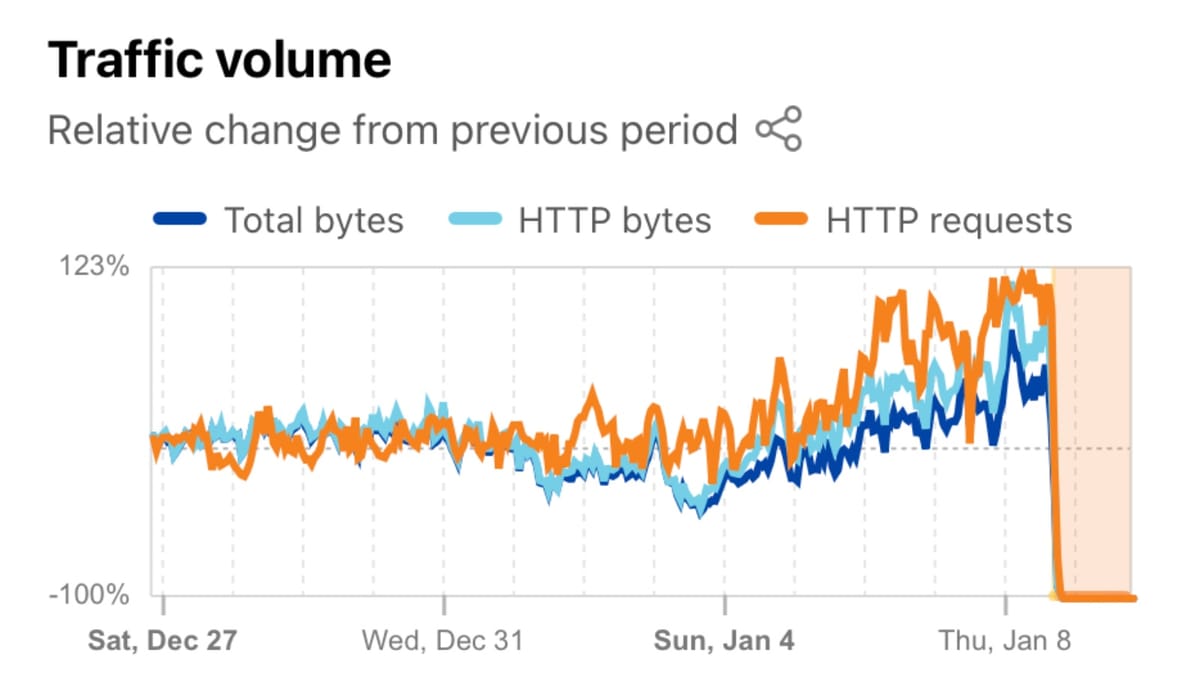
Internet infrastructure in Iran experienced catastrophic collapse on January 8, 2026, as government authorities implemented a nationwide shutdown that effectively severed digital connectivity for millions of citizens. The disruption began at 16:30 UTC (20:00 local time) and intensified rapidly, with network traffic plummeting nearly 90% in the subsequent 30 minutes, according to Cloudflare Radar data.
The technical sophistication of the shutdown became evident through multiple infrastructure manipulation tactics. Just before 12:00 UTC on January 8, the amount of announced IPv6 address space in Iran dropped by approximately 98.5%, concurrent with IPv6 traffic share declining from around 12% to 1.8%, according to Cloudflare Radar monitoring. This selective blocking demonstrates government control over routing infrastructure at the protocol level, effectively making Iranian networks invisible to the global internet.
Cloudflare Radar confirmed the nationwide scope, stating "Starting around 16:30 UTC (20:00 local time), traffic in #Iran began to drop rapidly, falling nearly 90% in the following 30 minutes. Declines were seen across major network providers." The timing coincided with intensifying protests across the country, following established patterns where Iranian authorities shut down internet access during periods of civil unrest.
Free weekly newsletter
Your go-to source for digital marketing news.
No spam. Unsubscribe anytime.
VPN services confirm infrastructure elimination
Virtual private network providers documented the shutdown from their own monitoring systems. Proton VPN reported on January 8 that "Proton VPN sessions originating in Iran are dipping, confirming the infrastructure which allows people to access the internet is being shut down." The company noted that "Normally, Proton VPN helps people affected by censorship to circumvent it, but in this case, the internet has been shut off entirely."
This distinction highlights the severity of the January 8 incident. Unlike typical censorship measures where VPN services can route around government blocks, complete infrastructure shutdowns eliminate the underlying connectivity that enables any form of internet access. When telecommunications companies withdraw routing announcements and power down network equipment, even sophisticated circumvention tools become ineffective.
NetBlocks, an organization tracking cybersecurity and digital governance, confirmed the nationwide nature of the blackout, stating "Confirmed: Live metrics show #Iran is now in the midst of a nationwide internet blackout; the incident follows a series of escalating digital censorship measures targeting protests across the country and hinders the public's right to communicate at a critical moment."
The technical infrastructure manipulation appeared coordinated across multiple autonomous systems. Major Iranian network providers including MCCI-AS (AS197207), IranCell-AS (AS44244), TCI (AS58224), negintel-as (AS56548), and RASANA (AS31549) all exhibited traffic declines. This multi-provider coordination suggests government directives implemented simultaneously across the telecommunications sector rather than isolated technical failures.
Buy ads on PPC Land. PPC Land has standard and native ad formats via major DSPs and ad platforms like Google Ads. Via an auction CPM, you can reach industry professionals.
Historical precedent and repeated patterns
Proton VPN noted on January 8 that "this is not the first time the Iranian people are witnessing a total shutdown of internet infrastructure." David Peterson, responding to questions about historical patterns, referenced connectivity data from June 2025, stating "From our stats, connections in Iran were totally out from the afternoon (UTC) of 18th June until the morning of the 21st; then some minimal connectivity until the morning of the 25th when it snapped back."
These recurring shutdown patterns align with documented government responses to domestic protests and civil unrest. Iranian authorities have deployed internet shutdowns as tactical tools to limit protest coordination and restrict information flow to international media organizations. The January 8 shutdown follows this established playbook, implemented at the precise moment when domestic demonstrations appeared to gain momentum.
Cloudflare Radar data visualizing announced IP address space in Iran showed IPv6 /48 allocations maintaining relatively stable levels around 45 million addresses throughout early January 2026, before collapsing dramatically to nearly zero on January 8 at approximately 13:45 UTC. The graph displaying this collapse reveals the technical precision of the government's infrastructure manipulation, with the sharp vertical drop indicating coordinated withdrawal of routing announcements rather than gradual technical degradation.
Traffic trends data from Cloudflare covering the two-week period from December 27, 2025, through January 8, 2026, shows normal cyclical patterns of total bytes, HTTP bytes, and HTTP requests until the sudden cessation on January 8. The visualization reveals regular daily fluctuations consistent with typical internet usage patterns—peaks during evening hours and valleys during overnight periods—until the unprecedented collapse that eliminated virtually all measurable traffic.
Technical infrastructure manipulation details
The multi-stage shutdown revealed sophisticated control over routing infrastructure. Initial IPv6 traffic drops began at 11:49 UTC, according to annotated Cloudflare data, with IPv6 traffic experiencing a preliminary decline. A second, more substantial drop occurred at 13:29 UTC, further degrading IPv6 connectivity before the comprehensive shutdown affecting all traffic types commenced at 16:30 UTC.
This phased approach suggests deliberate testing or progressive implementation rather than emergency actions. Government network operators likely verified control mechanisms on IPv6 infrastructure before extending restrictions to IPv4 traffic and implementing complete connectivity termination. The technical execution demonstrates institutional knowledge of network administration and routing protocols.
Regional traffic patterns within Iran remained consistent with historical distributions until the shutdown. Tehran accounted for 49.9% of HTTP requests, according to Cloudflare data, followed by Fars at 10%, Razavi Khorasan at 9.1%, East Azerbaijan at 8.9%, and Isfahan at 8.7%. This geographic distribution reflects population centers and economic activity, with the capital region representing approximately half of all internet traffic.
Mobile versus desktop traffic showed nearly even distribution at 49.7% mobile and 50.3% desktop, according to Cloudflare measurements. This balanced split differs from many developing markets where mobile traffic predominates, suggesting relatively high fixed-line broadband penetration in urban Iranian centers. Bot traffic accounted for 84% of HTTP requests, consistent with automated monitoring, API calls, and background services typical of modern internet traffic patterns.
Marketing and business continuity implications
Internet infrastructure disruptions create immediate challenges for digital marketing operations across affected regions. Government-directed shutdowns particularly impact programmatic advertising and real-time bidding systems that depend on consistent network connectivity. Iranian consumers became completely unreachable through digital advertising channels during the January 8 shutdown, rendering any campaigns targeting the market instantly ineffective.
Programmatic advertising relies on real-time connections between demand-side platforms, supply-side platforms, and advertising exchanges. Network connectivity enables the split-second auctions that determine which advertisements appear to users. Complete infrastructure elimination prevents these auctions from occurring, effectively halting all programmatic operations within the affected territory. Advertising spend allocated to Iranian inventory during the shutdown period delivered zero impressions and generated zero conversions.
Digital advertising campaigns require stable infrastructure foundations beyond just campaign optimization. When technical failures or government actions eliminate underlying connectivity, campaign sophistication becomes irrelevant. The Iranian shutdown demonstrates how political factors override technical capabilities, forcing marketing teams to account for governance risks when selecting target markets.
Geographic diversification in digital marketing campaigns provides some protection against localized disruptions. However, marketers targeting Iranian consumers face unique challenges, as recurring shutdown patterns make the market inherently unstable for sustained digital presence. Previous shutdown episodes in June 2025 demonstrated that connectivity losses can persist for days, creating extended periods of zero campaign performance.
Attribution modeling fails completely during infrastructure shutdowns. Conversion tracking requires network connectivity to transmit user actions from websites back to advertising platforms. Without internet access, users cannot complete conversions even if they intended to respond to previous advertising exposure. This breaks attribution chains and renders impossible the measurement methodologies that justify digital marketing investments.
The shutdown's economic impact extends beyond advertising to e-commerce, digital payments, and cloud-based business operations. Iranian merchants using international payment processors lost connectivity to authorization systems. Software-as-a-service platforms became inaccessible. Remote workers depending on cloud productivity tools found themselves completely offline. These cascading failures demonstrate how digital transformation creates vulnerabilities to state-directed infrastructure manipulation.
International response and digital rights concerns
Social media commentary reflected widespread concern about the humanitarian and political implications. One user stated "A new North Korea style lockdown has emerged in the Middle East," while another observer noted "This is a disturbing trend. Looks like the Iranian government is trying to isolate its citizens completely." These reactions highlight growing recognition of internet access as fundamental infrastructure rather than optional amenity.
Another commenter emphasized the historical context and human cost, stating "The Islamic terrorist regime in Iran has shut down the Internet because of the massive protests across the country. They have done this in the past and killed thousands of people." This perspective connects infrastructure shutdowns to broader patterns of government repression and violence against demonstrators, suggesting that digital isolation enables physical crackdowns by limiting documentation and international awareness.
Technical observers noted the precision of the government's implementation. One analyst commented "The 16:30 UTC timeline shows near real-time route manipulation. Any resilient system relying solely on global connectivity just got stress-tested." This observation underscores how state control of telecommunications infrastructure enables rapid, coordinated shutdowns that defeat technical resilience measures designed for natural disasters or equipment failures.
The incident demonstrates the limitations of circumvention technologies when governments control physical infrastructure. While VPN services, proxy servers, and encrypted communication tools provide protection against content filtering and surveillance, they cannot function without underlying internet connectivity. When telecommunications companies shut down transmission equipment or withdraw routing announcements under government order, no software solution can restore access.
Internet disruptions now account for significant portions of major connectivity problems globally. Government-directed shutdowns have evolved from rare emergency measures to routine tools for managing domestic political challenges. The Iranian pattern of recurring shutdowns during protest periods represents one extreme of this trend, but similar tactics have appeared across dozens of countries facing civil unrest or political transitions.
Free weekly newsletter
Your go-to source for digital marketing news.
No spam. Unsubscribe anytime.
Technical monitoring and global visibility
Cloudflare's network infrastructure provided comprehensive visibility into the Iranian shutdown. The company operates more than 330 cities across 125 countries with interconnections to over 13,000 network providers, positioning it to observe internet resilience patterns at local, national, and network levels. This global distribution enables detection of disruptions that might escape notice through more limited monitoring infrastructure.
The announced IP address space graph reveals the technical nature of the government's shutdown mechanism. Rather than physically disconnecting equipment, Iranian network operators withdrew Border Gateway Protocol announcements that inform the global internet how to reach Iranian IP addresses. This approach effectively makes Iranian networks invisible to international traffic while maintaining physical infrastructure intact for potential rapid restoration.
Traffic characteristic data showed bot traffic dominating at 84% versus 16% human traffic prior to the shutdown, consistent with automated systems maintaining persistent connections. This high bot proportion reflects modern internet architecture where applications continuously communicate with servers, API endpoints exchange data, and monitoring systems generate regular traffic independent of human users. The shutdown eliminated both human and automated traffic simultaneously.
Regional traffic distribution within Iran remained stable until the shutdown moment. Tehran's dominance at 49.9% of requests reflects the capital's concentration of population, businesses, and internet infrastructure. Secondary cities including Shiraz (Fars province), Mashhad (Razavi Khorasan), Tabriz (East Azerbaijan), and Isfahan each contributed between 8-10% of traffic, showing significant internet adoption beyond the capital while maintaining Tehran's clear leadership.
The HTTP traffic graph spanning late December 2025 through early January 2026 displays regular diurnal patterns with clear peaks and valleys corresponding to Iranian time zones. Evening peaks align with 20:00 local time when residential users maximize internet consumption, while overnight valleys reflect reduced activity during sleeping hours. This natural pattern continued until the abrupt cessation on January 8, highlighting the shutdown's artificial rather than organic nature.
Infrastructure dependencies and digital sovereignty
The Iranian shutdown illustrates fundamental tensions between digital globalization and state sovereignty. Internet protocols assume open, interconnected networks where routing decisions reflect technical efficiency rather than political control. Border Gateway Protocol, the system enabling global internet routing, operates on trust assumptions that network operators will announce accurate routing information and maintain connectivity unless technical failures intervene.
Governments controlling telecommunications infrastructure can subvert these technical assumptions. By issuing directives to licensed network operators, authorities can implement coordinated shutdowns that appear as widespread technical failures to external observers. The legal frameworks governing telecommunications in most countries grant governments broad authority over network operations, particularly during declared emergencies or national security situations.
Iranian telecommunications companies operate under domestic law and regulatory authority that supersedes international norms about internet openness. When government directives require shutdown implementation, these companies face legal obligations to comply regardless of international criticism or technical best practices. This creates structural vulnerability where internet connectivity depends entirely on domestic political decisions rather than technical considerations.
The technical precision demonstrated in the January 8 shutdown suggests institutional knowledge and practiced procedures. Network operators executed coordinated actions across multiple autonomous systems, withdrew routing announcements in phased sequences, and achieved near-total connectivity elimination within defined timeframes. This level of coordination requires planning, training, and established command structures rather than improvised responses.
Long-term patterns and future implications
The recurring nature of Iranian internet shutdowns establishes them as standard government tactics rather than extraordinary measures. The June 2025 shutdown lasted approximately three days according to VPN provider data, followed by partial restoration and eventual return to normal connectivity. The January 8, 2026 incident followed similar patterns, suggesting developed protocols for implementing and lifting restrictions.
Infrastructure stability affects long-term digital marketing viability in affected regions. International companies evaluating Iranian market opportunities must factor recurring shutdown risks into business planning. E-commerce operations cannot maintain customer relationships when connectivity disappears unpredictably. Software-as-a-service providers cannot guarantee availability when infrastructure access depends on political decisions.
The Iranian model of infrastructure control has attracted attention from other governments facing domestic unrest. Technical demonstrations of shutdown capabilities may encourage adoption elsewhere, particularly in countries with state-controlled or state-influenced telecommunications sectors. As internet penetration increases globally, more governments gain the technical means to implement similar restrictions.
Digital rights organizations face limited tools to counter infrastructure-level shutdowns. Legal challenges require domestic judicial systems that may support government actions. International pressure operates through diplomatic channels with limited enforcement mechanisms. Technical circumvention solutions cannot function without underlying connectivity. This asymmetry between state control of physical infrastructure and civil society's defensive capabilities creates structural advantages for authorities implementing restrictions.
The incident reinforces the importance of satellite internet technologies and alternative connectivity solutions that bypass terrestrial telecommunications infrastructure. Starlink and similar satellite internet systems could theoretically provide connectivity during terrestrial shutdowns, though governments may prohibit satellite terminal possession or implement jamming. The technical and legal complexities of maintaining internet access against determined government opposition remain substantial.
Subscribe PPC Land newsletter ✉️ for similar stories like this one
Timeline
- June 18-25, 2025: Iran experienced previous total internet shutdown lasting several days, with minimal connectivity between June 21-25 before full restoration
- January 8, 2026, 11:49 UTC: Initial drop in IPv6 traffic detected in Iran, marking beginning of infrastructure manipulation
- January 8, 2026, 12:00 UTC: Approximately 98.5% of announced IPv6 address space in Iran withdrawn, with IPv6 traffic share dropping from 12% to 1.8%
- January 8, 2026, 13:29 UTC: IPv6 traffic experiences further substantial decline as government control mechanisms expand
- January 8, 2026, 16:30 UTC (20:00 local time): Comprehensive shutdown affecting all traffic types begins, with traffic dropping nearly 90% within 30 minutes across major network providers
- January 8, 2026, 18:43 UTC: Proton VPN confirms Iranian internet sessions dropping, noting infrastructure allowing internet access being shut down entirely
- January 8, 2026, 18:11 UTC: Cloudflare Radar publishes confirmation of rapid traffic decline, noting 90% reduction and major provider involvement
- Ongoing: Global internet traffic grew 17% in 2024, though recurring disruption challenges affect marketing operations in unstable regions
Subscribe PPC Land newsletter ✉️ for similar stories like this one
Summary
Who: Iranian government authorities directed telecommunications companies including MCCI-AS, IranCell-AS, TCI, negintel-as, and RASANA to implement nationwide internet shutdown. Millions of Iranian citizens lost internet access. Proton VPN, NetBlocks, and Cloudflare Radar documented the shutdown through monitoring systems.
What: Iranian network operators withdrew approximately 98.5% of announced IPv6 address space and implemented comprehensive connectivity shutdown that reduced internet traffic by nearly 90% within 30 minutes. The shutdown employed sophisticated routing manipulation affecting both IPv4 and IPv6 protocols, coordinated across multiple major telecommunications providers. VPN services became ineffective as underlying infrastructure was eliminated rather than merely filtered.
When: The shutdown began with initial IPv6 manipulation at 11:49 UTC on January 8, 2026, escalated with major IPv6 address space withdrawal at 12:00 UTC, and culminated in comprehensive traffic elimination starting at 16:30 UTC (20:00 Iranian local time). The incident followed previous shutdown patterns including a June 2025 episode lasting approximately three days.
Where: The shutdown affected all of Iran nationwide, with monitoring data showing traffic declines across major regions including Tehran (49.9% of previous traffic), Fars (10%), Razavi Khorasan (9.1%), East Azerbaijan (8.9%), and Isfahan (8.7%). Cloudflare's global network with presence in 330 cities across 125 countries documented the disruption through direct observation of routing changes and traffic measurements.
Why: The government implemented the shutdown concurrent with spreading protests across Iran, following established patterns where authorities eliminate internet access during civil unrest to limit protest coordination and restrict information flow to international observers. The technical sophistication and phased implementation suggest planned response rather than emergency reaction. Previous shutdowns in June 2025 established protocols that authorities repeated during the January 8 incident, with infrastructure control enabling near-total digital isolation within minutes of directive issuance.

