Meta detailed its development of an agentic solution for data warehouse access and security during a presentation at the @Scale conference on August 13, 2025. Software engineers Can Lin and Uday Ramesh Savagaonkar outlined how the company addresses data access complexity for billions of users and tens of thousands of engineers using artificial intelligence agents.
The announcement comes as enterprise organizations grapple with growing data access complexity. According to Can Lin, "meta operates large scale data warehouse in the era of agents how does its data access evolve." The engineers explained how traditional hierarchical access management struggles to scale with AI-driven workflows requiring cross-domain data analysis.
Subscribe the PPC Land newsletter ✉️ for similar stories like this one. Receive the news every day in your inbox. Free of ads. 10 USD per year.
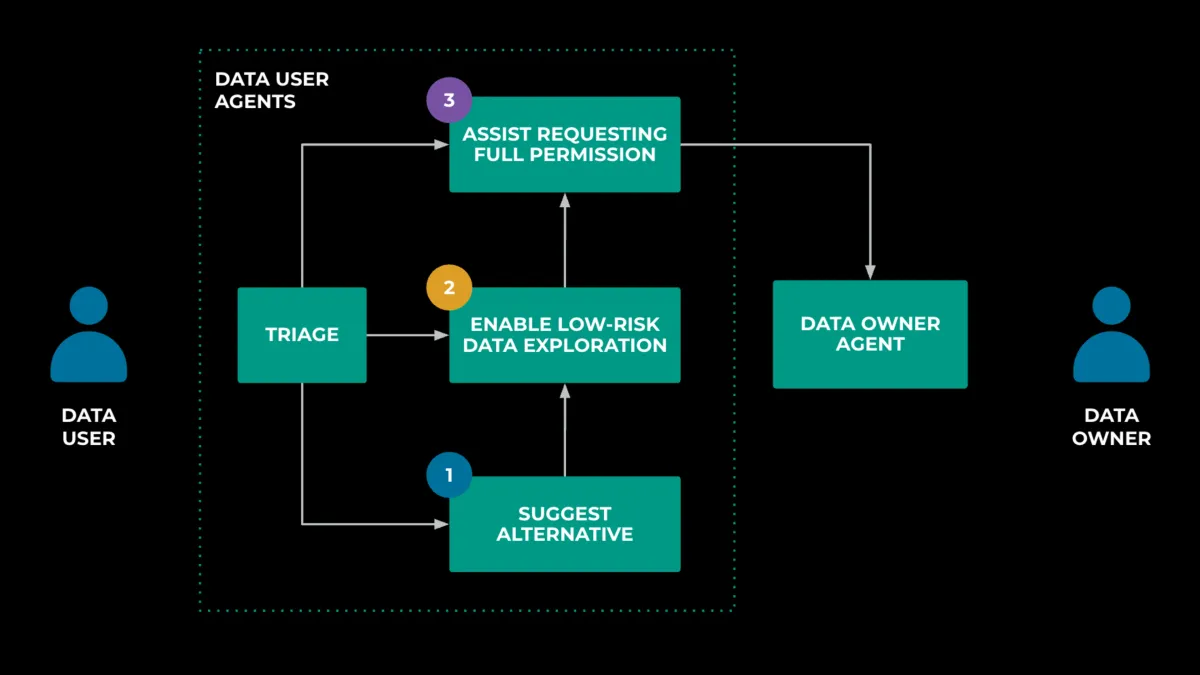
Meta's solution introduces a multi-agent system comprising data user agents and data owner agents. These specialized systems negotiate access requests automatically while maintaining security protocols. The data user agent consists of three sub-agents: one suggesting alternatives when access restrictions occur, another enabling low-risk data exploration, and a third assisting with permission requests.
According to the presentation, the data owner agent includes two sub-agents focused on security operations and access management. Lin explained that the security operation agent "operates like a junior engineer and when they join a team they follow the SOP standard operating procedure which documents how the access should be managed."
The system addresses key enterprise challenges identified in current market research. Marketing automation concerns over AI infrastructure requirements have prompted organizations to seek more sophisticated data access solutions. McKinsey's Technology Trends Outlook 2025 identified agentic AI as a primary transformation driver affecting organizational data strategies.
Meta's implementation requires significant infrastructure evolution. The engineers described transforming the hierarchical data warehouse structure into a text-based format compatible with large language models. "LLMs communicate through text so the hierarchical structure of data warehouse nicely mapped to a folder structure," Savagaonkar explained during the presentation.
Context management represents another critical component. The system differentiates between automatic context when users encounter access blocks, static context for explicit scope selection, and dynamic context enabling resource filtering through metadata and similarity search. This approach enables more precise access decisions compared to traditional role-based systems.
The presentation detailed intention management capabilities that model business needs through explicit and implicit methods. Explicit intention involves users communicating their tasks to the system by assuming specific roles. Implicit intention derives from user activities over short periods, such as responding to pipeline failures requiring immediate data access.
Performance metrics demonstrate the system's effectiveness. According to Savagaonkar, "our overall recall rate is 90% with acceptance recall rate of 73% and rejection recall rate of 100%." The acceptance rate means 73% of users gained immediate access without manual approval processes, while data owner workload decreased by the same percentage.
The evaluation process utilizes historical access request data including user justifications, human decisions, and subsequent query patterns. This dataset enables continuous system improvement through feedback loops and model fine-tuning. All queries and requests undergo logging in secure systems for auditing and quality monitoring.
Partial data preview functionality exemplifies the end-to-end implementation. This capability addresses the data exploration phase where users typically need small data samples to evaluate usefulness. The system implements four key capabilities: context-driven decisions, fine-grained query-level permissions, data access budgets, and rule-based safeguarding.
Data access budgets provide daily renewable limits protecting against overexposure while enabling legitimate exploration. Query-level access control analyzes query shapes including aggregation patterns and sampling methods. Rule-based safeguarding serves as the final defense against AI agent errors or malicious attempts.
The announcement addresses growing industry concerns about AI reliability in enterprise environments. Recent studies show 20% error rates in AI responses for marketing strategy questions, highlighting the need for robust guardrails in business-critical applications.
Security considerations remain paramount throughout Meta's implementation. The system maintains human oversight while gradually increasing agent autonomy. Transparency and decision tracing enable audit compliance while protecting sensitive user data across the platform's infrastructure.
Consumer privacy concerns influence enterprise AI development strategies. European research reveals 59% opposition to AI training data use, creating pressure for transparent data handling practices in automated systems.
The agentic approach represents Meta's response to increasing system complexity driven by AI adoption. Traditional access patterns involved localized decisions within team hierarchies. Modern AI systems process data across unrelated sources, requiring sophisticated authorization mechanisms that human operators cannot efficiently manage.
Future development priorities include agent collaboration scenarios where AI systems access data on behalf of users rather than direct human interaction. Infrastructure evolution continues adapting systems originally designed for employees and services to support autonomous agent operations.
Evaluation and benchmarking development ensures continuous improvement as the technology matures. The company emphasizes the importance of ongoing assessment to maintain system reliability and security standards as agent capabilities expand.
Meta's announcement reflects broader industry movement toward agentic AI implementation in enterprise environments. IBM's watsonx Orchestrate platform addresses similar enterprise compliance requirements through standardized frameworks and audit capabilities necessary for regulated industries.
The presentation occurred during a period of increased focus on AI infrastructure investment. Meta announced unprecedented AI infrastructure investment with gigawatt-scale data centers demanding substantial energy consumption to support advanced AI capabilities.
Industry competition intensifies as organizations develop agentic AI solutions. The @Scale conference presentation positions Meta's approach as a comprehensive solution addressing both security and productivity requirements in large-scale data environments.
Subscribe the PPC Land newsletter ✉️ for similar stories like this one. Receive the news every day in your inbox. Free of ads. 10 USD per year.
Timeline
- August 13, 2025: Meta announces agentic solution for data warehouse access at @Scale conference
- July 2025: McKinsey identifies agentic AI as primary transformation driver in Technology Trends Outlook 2025
- July 10, 2025: WordStream study reveals 20% error rates in AI responses for PPC strategy questions
- July 9, 2025: StackAdapt launches Ivy AI assistant for marketing automation
- July 1, 2025: European study shows 59% consumer opposition to AI training data use
- March 27, 2025: Zeta Global announces AI Agent Studio general availability
- October 15, 2024: Treasure Data unveils AI Framework for CDP at CDP World 2024
Subscribe the PPC Land newsletter ✉️ for similar stories like this one. Receive the news every day in your inbox. Free of ads. 10 USD per year.
PPC Land explains
Agentic AI: Artificial intelligence systems that operate autonomously to plan and execute complex workflows without constant human supervision. Unlike traditional AI that responds to specific prompts, agentic AI creates virtual collaborators capable of managing entire processes, from data discovery to access approval, while adapting strategies based on real-time conditions and organizational policies.
Data Warehouse: Large-scale repository systems that store and organize vast amounts of structured and unstructured data from multiple sources within an organization. Meta's data warehouse supports analytics, machine learning, and AI use cases across billions of users, requiring sophisticated access management to balance security requirements with operational efficiency.
Multi-Agent System: Coordinated network of specialized AI agents working together to complete complex business processes, where each agent focuses on specific tasks while communicating with other agents to achieve broader objectives. This approach enables organizations to automate intricate workflows spanning multiple departments and data sources through interconnected artificial intelligence systems.
Access Control: Security framework that determines which users or systems can access specific data resources based on predetermined policies, roles, and contextual factors. Traditional role-based access control relies on hierarchical structures, while modern systems incorporate AI-driven decision-making to handle complex cross-domain data requirements that exceed human management capabilities.
Context Management: Systematic approach to organizing and providing relevant information to AI systems to improve their decision-making accuracy and effectiveness. This encompasses automatic context from blocked access attempts, static context from explicit user selections, and dynamic context through metadata filtering and similarity search capabilities.
Query-Level Permissions: Fine-grained access control mechanism that analyzes individual database queries to determine appropriate data exposure based on query structure, aggregation patterns, and sampling methods. This granular approach enables more precise security decisions compared to traditional table-level or column-level permissions, particularly important for exploratory data analysis workflows.
Standard Operating Procedures (SOP): Documented guidelines and rules that define how data access should be managed within specific teams or organizational units. These procedures, derived from established policies, historical decisions, and tribal knowledge, become machine-readable resources that guide AI agents in making consistent access decisions aligned with organizational security practices.
Large Language Models (LLMs): Advanced AI systems trained on vast amounts of text data to understand and generate human-like language, enabling communication between AI agents and existing enterprise systems. In data warehouse contexts, LLMs process hierarchical organizational structures, analyze business justifications, and generate access recommendations based on contextual understanding of user needs and security requirements.
Data Exploration: Preliminary phase of data analysis where users examine small samples of datasets to determine relevance and usefulness before committing to full-scale analysis projects. This phase traditionally creates friction because users must request access to data they may ultimately not use, while data owners must process requests for potentially unnecessary access grants.
Enterprise Infrastructure: Technological foundation comprising computing power, data storage, networking capabilities, and security systems necessary to support organizational operations at scale. The shift toward AI-powered data tools creates unprecedented demands on infrastructure, particularly for real-time processing and analysis of user interactions while maintaining performance and reliability standards.
Subscribe the PPC Land newsletter ✉️ for similar stories like this one. Receive the news every day in your inbox. Free of ads. 10 USD per year.
Summary
Who: Meta software engineers Can Lin and Uday Ramesh Savagaonkar presenting at the @Scale conference, addressing data access challenges for billions of users and tens of thousands of engineers.
What: Multi-agent system for data warehouse access featuring data user agents and data owner agents that automatically negotiate permissions while maintaining security protocols and reducing manual approval processes.
When: Announced August 13, 2025, at the @Scale conference, with development occurring throughout 2025 as enterprise AI adoption accelerated across Meta's infrastructure.
Where: Implemented across Meta's large-scale data warehouse supporting analytics, machine learning, and AI use cases, with global implications for enterprise data access management.
Why: Traditional hierarchical access management cannot scale with AI-driven workflows requiring cross-domain data analysis, necessitating automated systems that maintain security while enabling productivity for complex data access patterns.

