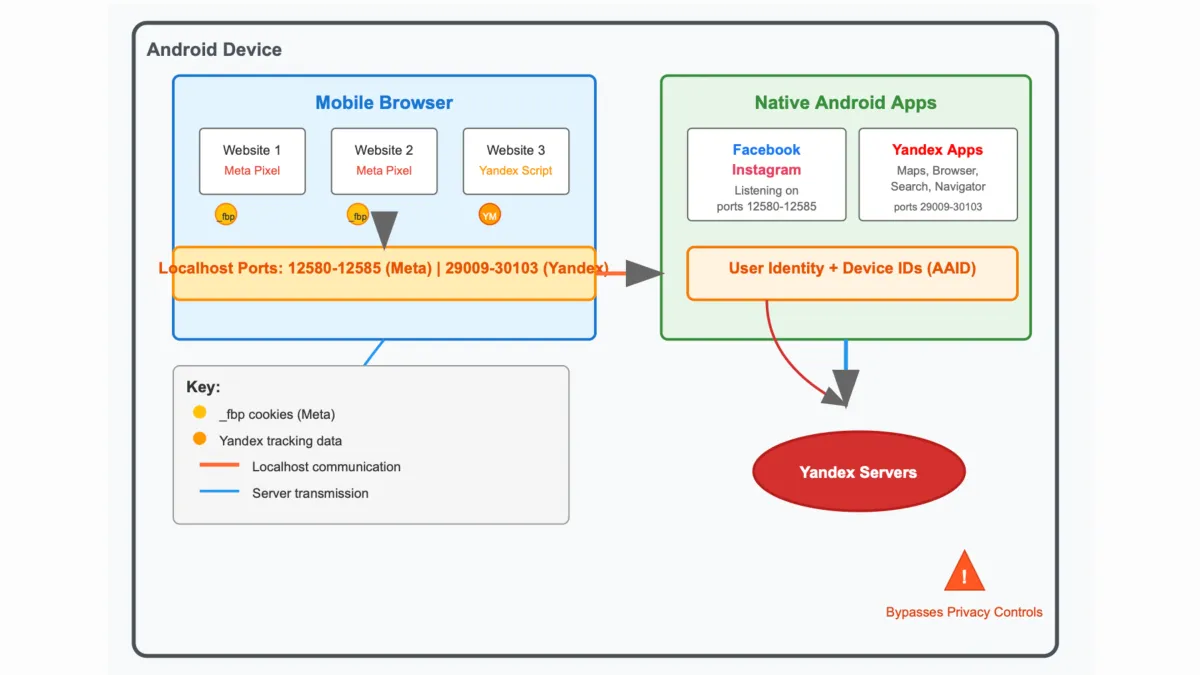
A team of academic researchers disclosed a novel tracking technique used by Meta that affected potentially billions of Android users. According to the research report titled "Covert Web-to-App Tracking via Localhost on Android," native Android apps—including Facebook, Instagram, and several Yandex apps including Maps and Browser—silently listen on fixed local ports for tracking purposes.
Get the PPC Land newsletter ✉️ for more like this
The discovery, made public on June 3, 2025 (four days ago), prompted immediate action from Meta. As of June 3rd 7:45 CEST, Meta/Facebook Pixel script is no longer sending any packets or requests to localhost. The code responsible for sending the _fbp cookie has been almost completely removed.
The tracking method exploited Android's localhost socket system to create an unauthorized communication channel between web browsers and native applications. The Android OS allows any installed app with the INTERNET permission to open a listening socket on the loopback interface (127.0.0.1). Browsers running on the same device also access this interface without user consent or platform mediation.
Related Stories
- Meta confronts EU watchdog on "beyond the law" compliance demands - March 8, 2025
- IAS and DoubleVerify expand Brand Safety controls on Meta platforms - October 13, 2024
- Meta's CrowdTangle to shut down in August 2024 - March 16, 2024
Meta's implementation specifically targeted the _fbp cookie through a sophisticated process. The Meta (Facebook) Pixel JavaScript, when loaded in an Android mobile web browser, transmits the first-party _fbp cookie using WebRTC to UDP ports 12580–12585 to any app on the device that is listening on those ports. According to the research findings, Meta-owned Android apps Facebook (version 515.0.0.23.90) and Instagram (version 382.0.0.43.84), available on the Google Play Store, listening on these port range.
Technical implementation evolved over time, according to the research findings. As of 25 2025, the Meta Pixel uses a technique known as SDP Munging to insert the _fbp cookie contents to the SDP "ice-ufrag" field, resulting in a Binding Request STUN message sent to the loopback address. Later iterations included additional protocols. On or around May 17th, Meta Pixel added a new method to their script that sends the _fbp cookie using WebRTC TURN instead of STUN.
The prevalence of this tracking method extended across millions of websites globally. According to BuiltWith, a website that tracks web technology adoption: Meta Pixel is embedded on over 5.8 million websites. More conservative estimates from HTTP Archive data show Meta Pixel and Yandex Metrica are present on 2.4 million and 575,448 websites, respectively.
Researchers conducted comprehensive crawls to measure real-world implementation. The following table shows the number of sites found affected for each case. The first column for each region shows the number of sites embedding these trackers when accepting all cookie consent forms. The second column (labeled as "no consent") reports the number of sites actively attempting to perform localhost communications by default as soon as the user loads them on their browser, i.e., potentially without user consent.
Meta Pixel 17,223 13,468 (78.2%) 15,677 11,890 (75.8%) for US and Europe respectively, indicating widespread deployment without explicit user consent.
The tracking methods were not new developments but had extended operational periods. Meta HTTP Sep 2024 Oct 2024* 12387 marked the beginning of Meta's localhost tracking, while Yandex HTTP Feb 2017 - 29009, 30102 showed that Yandex had been employing similar techniques since February 2017.
Meta's approach became increasingly sophisticated over time. WebRTC STUN (w/ SDP Munging) Nov 2024 - 12580-12585 represented their most recent active implementation, while WebRTC TURN** (w/o SPD Munging) May 2025 - 12586-12591 showed preparation for future methods.
Multiple browser vendors responded to the disclosure with security patches. Chrome 136.0.7103.125 Affected Affected Version 137, released on 26 May 2025, shipped countermeasures to block abused ports and disable the specific form of SDP munging that Meta Pixel used.
Mozilla implemented similar protections. Firefox 138.0.2 Affected Not affected. Version 139 will include countermeasures to block the ports involved. Some browsers already had existing protections that prevented the tracking. Brave 1.78.102 Not affected Not affected Not affected. Localhost communications require user consent since 2022, and implements a blocklist.
Bypass of existing privacy protections
The tracking method circumvented traditional privacy safeguards that users typically rely upon. This web-to-app ID sharing method bypasses typical privacy protections such as clearing cookies, Incognito Mode and Android's permission controls. This tracking method defeats Android's inter-process isolation and tracking protections based on partitioning, sandboxing, or clearing client-side state.
The implications extended beyond simple cookie tracking. However, the method we disclose allows the linking of the different _fbp cookies to the same user, which bypasses existing protections and runs counter to user expectations.
Potential GDPR violations and regulatory exposure
The localhost tracking methods disclosed in the research report may constitute serious violations of the European Union's General Data Protection Regulation (GDPR), potentially exposing both Meta and Yandex to substantial financial penalties. The GDPR framework, which came into effect in May 2018, establishes strict requirements for data processing that the localhost tracking appears to violate across multiple provisions.
The most fundamental GDPR violation concerns lawful basis for processing under Article 6. The research findings indicate that both companies collected and processed personal data without establishing a proper legal foundation. According to the study, preliminary results suggest that these practices may be implemented in websites without explicit and appropriate cookie consent forms, meaning users never provided informed consent for this data collection method.
Article 5 of GDPR mandates that personal data processing must be transparent, yet the localhost tracking operated in complete secrecy. The research report found no public documentation by Meta or Yandex describing this method and its purpose, directly contradicting the transparency principle. When website developers discovered localhost connections and sought explanations, they received no official responses from Meta representatives, further demonstrating the covert nature of these operations.
The principle of data minimization under Article 5 requires that data collection be limited to what is necessary for specified purposes. However, the localhost tracking captured comprehensive browsing behavior across millions of websites. As the researchers noted, the information collected extends far beyond simple page visits to include detailed user actions: searches, shopping cart additions, purchases, and registrations across participating websites.
Purpose limitation violations emerge from the bridging of separate data contexts without user awareness. The research demonstrates that Meta linked different _fbp cookies to the same user, effectively creating cross-site tracking profiles that users explicitly sought to prevent through privacy-protective browsing behaviors. This data combination serves advertising purposes that users had not consented to when providing information to individual websites.
The technical implementation also violated data protection by design and by default requirements under Article 25. Rather than implementing privacy-protective measures, both companies designed systems that actively circumvented existing privacy controls. The tracking method specifically defeated Android's inter-process isolation and tracking protections based on partitioning, sandboxing, and clearing client-side state.
Under GDPR's penalty framework established in Article 83, regulatory authorities can impose administrative fines up to 20 million euros or four percent of total worldwide annual turnover, whichever is higher. For Meta, which reported total revenue of 134.9 billion dollars in 2023, the maximum potential fine could reach approximately 5.4 billion euros. Yandex, while smaller in scale, could still face penalties reaching hundreds of millions of euros based on their global revenue.
The scale of potential violations amplifies the financial exposure significantly. The research identified localhost tracking attempts on 17,223 websites in the United States and 15,677 websites in Europe for Meta Pixel alone. Each unauthorized data collection instance across millions of users could constitute a separate violation, creating cumulative penalty exposure that far exceeds the basic calculation framework.
European data protection authorities have demonstrated willingness to impose substantial fines for tracking violations. The Irish Data Protection Commission previously fined Meta 390 million euros for advertising consent violations, while French authorities imposed 60 million euros in penalties for cookie-related infractions. The localhost tracking disclosure represents violations that are arguably more severe than these previous cases due to their systematic circumvention of user privacy controls.
The cross-border nature of the localhost tracking creates jurisdiction complications that could result in multiple enforcement actions. The research documented tracking implementations across both European and American websites, suggesting that multiple European data protection authorities could initiate parallel investigations and penalty proceedings.
Additional security risks
Beyond privacy concerns, the localhost communication method created potential attack vectors for malicious applications. Using HTTP requests for web-to-native ID sharing (i.e. not WebRTC STUN or TURN) may expose users browsing history to third-parties. A malicious third-party Android application that also listens on the aforementioned ports can intercept the HTTP requests sent by the Yandex Metrica script.
The researchers demonstrated this vulnerability through practical testing. According to the report, "We developed a proof-of-concept app to demonstrate the feasibility of this browsing history harvesting by a malicious third-party app. We found that browsers such as Chrome, Firefox and Edge are susceptible to this form of browsing history leakage in both default and private browsing modes."
Get the PPC Land newsletter ✉️ for more like this
Company responses and industry reactions
Meta's initial response suggested ongoing discussions with Google regarding policy interpretations. "We are speaking with Google to clarify a potential misunderstanding about how its policies are applied. As soon as we learned of the concern, we decided to pause the feature while we work with Google to resolve the issue," said a Meta spokesperson.
Google confirmed the severity of the security findings. "The developers mentioned in this report are unintentionally using functions present in many iOS and Android browsers, which blatantly violate our security and privacy principles. We have already implemented changes to mitigate these invasive techniques, launched our own investigation, and are in direct contact with the parties involved."
Mozilla also expressed concern about the tracking practices. "We consider these to be severe violations of our anti-tracking policies," said a spokesperson from Mozilla Foundation. "Researchers have found that native Android apps — including Facebook, Instagram, and several Yandex apps such as Maps, Navi, Browser, Search — appear to misuse app-privileges in Android platform together with malicious online scripts to track people online."
Lack of documentation and transparency
The tracking implementation operated without public documentation or user awareness. We do not find any public documentation by Meta or Yandex' official documentation describing this method and its purpose. When website developers encountered unusual localhost connections, they received minimal support. For Meta Pixel, we found several complaints from puzzled website owners questioning why Meta Pixel communicates with localhost in Facebook developer forums by September 2024.
Developer frustration emerged in forum discussions where One developer stated in Sept. 2024: "No acknowledgement has come from Meta at all on this though. My support request with them got a generic response and then ignored thereafter." "It's a shame accountability hasn't been taken, we rely on these tools to work properly and have no control over them so at the very least we should be given an explanation on what went wrong."
Research methodology and disclosure process
The investigation began from unexpected localhost connections discovered during routine website analysis. According to El País reporting, Online privacy and tracking professor Günes Acar, from Radboud University in the Netherlands, wanted to have some fun with his master's students, so he started looking for an unusual example of tracking on his university's website: "I knew the page had several trackers, including Facebook's. But suddenly I saw a connection to a local port — in other words, to my own computer. At first, I didn't understand anything."
The research team expanded their investigation after initial discoveries. Acar discussed the case with Narseo Vallina-Rodríguez, a researcher at Imdea Networks and a specialist in mobile app security and privacy. "How the hell…," was his first reaction. Could Meta be trying something new to bypass browser privacy permissions?
The researchers followed responsible disclosure protocols, notifying major stakeholders before public release. Our responsible disclosure to major Android browser vendors led to several patches attempting to mitigate this issue; some already deployed, others currently in development.
Why this matters
This disclosure significantly impacts how marketers understand cross-device tracking capabilities and privacy compliance. The revelation demonstrates that traditional privacy controls may be insufficient against sophisticated tracking implementations that operate at the system level rather than within browser environments.
For marketing professionals, this incident highlights the importance of understanding the technical mechanisms behind advertising pixels and analytics tools. The ability to link mobile browsing behavior with logged-in user identities represents a powerful targeting capability, but one that operated without explicit user consent or awareness.
The immediate cessation of these practices following public disclosure suggests that privacy concerns and regulatory pressure continue to shape the boundaries of acceptable tracking technologies. Marketing teams must now consider whether their tracking implementations comply not only with stated policies but also with user expectations of privacy.
The incident also underscores the evolving nature of digital privacy enforcement, where technical capabilities may advance faster than regulatory frameworks or industry standards can address them.
Get the PPC Land newsletter ✉️ for more like this
Timeline
February 2017: Yandex begins localhost tracking implementation across Android applications
September 2024: Meta introduces localhost tracking methods for Facebook and Instagram applications on Android devices
September 2024: Website developers begin reporting unusual localhost connections in Facebook developer forums without receiving official responses
November 2024: Meta transitions to WebRTC STUN protocol with SDP Munging techniques for cookie transmission
May 17, 2025: Meta adds WebRTC TURN protocol capabilities to tracking infrastructure
May 26, 2025: Google releases Chrome 137 with preliminary countermeasures against SDP Munging
June 2, 2025: Academic researchers publish findings on covert web-to-app tracking methods
June 3, 2025: Meta halts localhost tracking practices and removes associated code

