According to OECD research published in March 2023, privacy-enhancing technologies enable collection, processing, analysis and sharing of information while protecting data confidentiality. The organization emphasizes these digital technologies permit relatively high utility from data while minimizing collection and processing requirements.
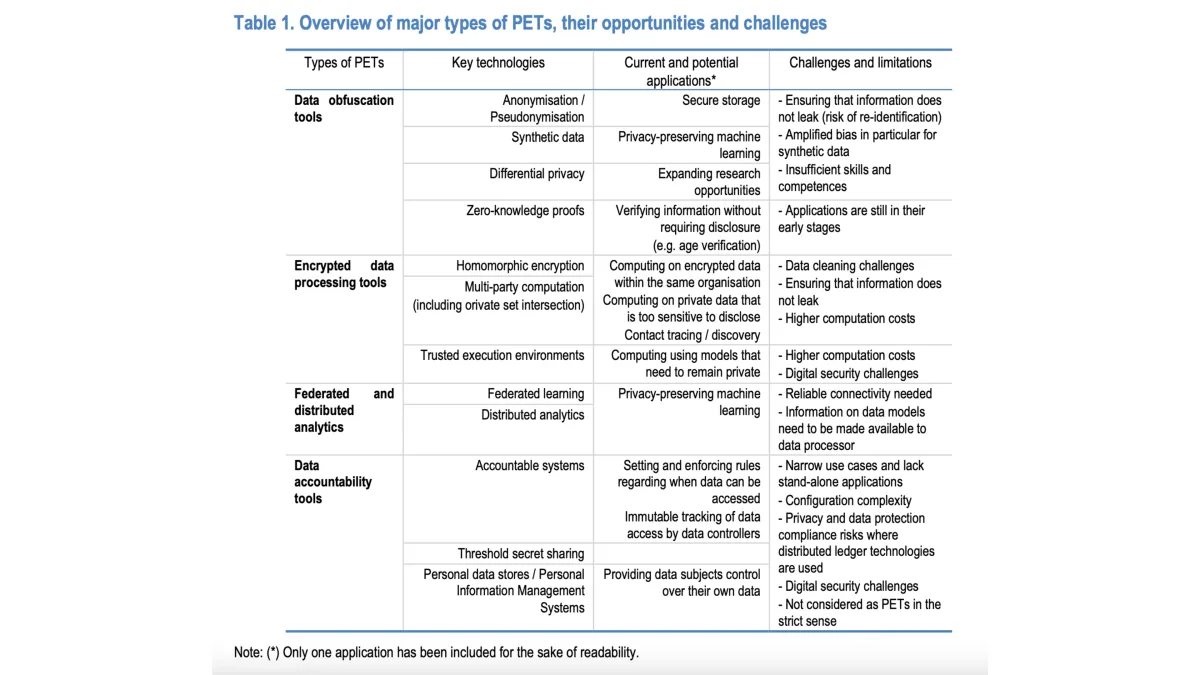
OECD analysis identifies four categories of privacy-enhancing technologies: data obfuscation tools, encrypted data processing tools, federated and distributed analytics, and data accountability tools. Each category addresses specific aspects of the OECD Privacy Guidelines' basic principles.
Subscribe the PPC Land newsletter ✉️ for similar stories like this one. Receive the news every day in your inbox. Free of ads. 10 USD per year.
Data obfuscation tools encompass anonymization, pseudonymization, synthetic data generation, differential privacy, and zero-knowledge proofs. These technologies alter data by adding noise or removing identifying details. According to the research, these tools enable privacy-preserving machine learning and information verification without requiring sensitive data disclosure.
The findings reveal encrypted data processing tools, including homomorphic encryption and multi-party computation, represent the most significant advancement in private data processing. These technologies allow computations over data that remain encrypted, addressing traditional vulnerabilities when data require decryption for processing.
Federated and distributed analytics permit executing analytical tasks on data not visible to processors. OECD research indicates federated learning reduces the need for sensitive data to leave devices, with only summary statistics transferred to data controllers.
The analysis highlights data accountability tools provide controls over data gathering and usage. These systems manage data use, track compliance, and establish rules for data access. OECD researchers note these tools traditionally fall outside strict privacy-enhancing technology definitions but enhance privacy through control mechanisms.
Technical limitations present significant challenges. The research identifies computation costs as substantially higher for encrypted data processing compared to standard database operations. Organizations avoid these techniques when simpler processing remains available.
Data cleaning challenges emerge with encrypted processing tools. OECD findings indicate analysts cannot examine encrypted data for quality control, requiring pre-processing checks at the data source level before submission.
Information leakage risks persist across multiple technology categories. According to the analysis, obfuscation measures can unintentionally expose information despite protective mechanisms. The research emphasizes no agreed-upon standards exist for required noise levels across different scenarios.
Regulatory frameworks increasingly recognize privacy-enhancing technologies. OECD research documents legal requirements for data protection by design across multiple jurisdictions. The European Union's General Data Protection Regulation Article 25 mandates appropriate technical measures for data protection by default.
Implementation approaches vary significantly between countries. According to OECD findings, some jurisdictions rely on best practices and guidance rather than mandatory requirements. Canada's federal Privacy Act lacks specific privacy-enhancing technology provisions but applies privacy-by-design principles through institutional best practices.
De-identification requirements create regulatory pathways for technology adoption. OECD analysis reveals varying standards between anonymization and pseudonymization across legal frameworks. The research indicates anonymized data falls outside privacy regulation scope in many jurisdictions while pseudonymized data remains subject to protection requirements.
Innovation initiatives proliferate across OECD countries. The analysis documents research funding programs, secure processing platforms, certification schemes, innovation contests, and regulatory sandboxes. These initiatives aim to foster technology development while addressing implementation barriers.
The United Kingdom's Information Commissioner's Office published comprehensive guidance on privacy-enhancing technologies in September 2022. This guidance examines homomorphic encryption, secure multi-party computation, federated learning, trusted execution environments, and zero-knowledge proofs across multiple sectors.
Singapore launched a privacy-enhancing technology sandbox through the InfoComm Media Development Authority and Personal Data Protection Commission in July 2022. The sandbox provides testing environments for piloting technology projects while identifying appropriate solutions for data-sharing objectives.
Cross-border data transfer applications present both opportunities and constraints. OECD research indicates privacy-enhancing technologies can facilitate transfers where traditional methods prove insufficient. However, regulatory uncertainty persists regarding technology acceptance for compliance purposes.
Current deployment remains limited despite technological advances. According to the findings, most applications operate at small scales with narrow use cases. The research attributes limited adoption to high costs, insufficient technical expertise, and unclear regulatory acceptance.
Skills and competence gaps hinder broader implementation. OECD analysis reveals complex anonymization processes require trained data scientists to prevent unintentional information leakage. Many organizations lack necessary resources for proper implementation.
Business adoption faces multiple barriers beyond technical limitations. The research identifies organizational resistance to changing established data processing paradigms. Privacy-enhancing technologies require significant upfront investments without guaranteed returns.
Regulatory coordination challenges emerge across multiple jurisdictions. OECD findings indicate varying implementation approaches create compliance complexities for organizations operating internationally. Harmonized standards remain elusive despite common underlying principles.
Future development depends on addressing current limitations while building stakeholder confidence. The research emphasizes need for standardized evaluation frameworks, improved cost-effectiveness, and clearer regulatory guidance. Technical advances must align with practical deployment requirements.
Privacy-enhancing technologies represent fundamental shifts in data processing paradigms rather than incremental improvements. OECD analysis positions these technologies as foundations for privacy by design implementation while acknowledging substantial development requirements remain.
Subscribe the PPC Land newsletter ✉️ for similar stories like this one. Receive the news every day in your inbox. Free of ads. 10 USD per year.
Timeline
- March 2023: OECD publishes "Emerging Privacy Enhancing Technologies: Current Regulatory and Policy Approaches"
- September 2024: IAB Tech Lab launches PAIR protocol for first-party data matching
- September 2024: Google introduces Confidential Matching to enhance advertiser data
- October 2024: IAB Tech Lab unveils ADMaP: a privacy-first digital ad attribution protocol
- December 2024: Google enables IP address targeting with new privacy technology in 2025
- December 2024: Google updates platform policies with focus on privacy and emerging ad surfaces
- January 2025: DV360: New tools for privacy-focused advertising
- January 2025: Major privacy breakthrough transforms digital advertising data sharing
- February 2025: Programmatic advertising growth reaches 72%
- April 2025: Google's latest privacy technologies for digital advertising
Subscribe the PPC Land newsletter ✉️ for similar stories like this one. Receive the news every day in your inbox. Free of ads. 10 USD per year.
Summary
Who: The OECD (Organization for Economic Cooperation and Development), privacy enforcement authorities, technology companies, and marketing organizations worldwide are involved in developing and implementing privacy-enhancing technologies.
What: Privacy-enhancing technologies (PETs) are digital solutions that enable data collection, processing, analysis and sharing while protecting confidentiality. These include data obfuscation tools, encrypted data processing, federated analytics, and data accountability systems.
When: The OECD published its comprehensive analysis in March 2023, building on technology developments that accelerated following privacy regulation implementation over the past decade.
Where: Implementation spans multiple jurisdictions globally, with varying regulatory approaches across OECD member countries including the United States, European Union, United Kingdom, Canada, Australia, Japan, and Singapore.
Why: Organizations require privacy-enhancing technologies to comply with evolving data protection regulations while maintaining analytical capabilities for business operations. These technologies address the fundamental tension between data utility and privacy protection in an increasingly regulated environment.
Subscribe the PPC Land newsletter ✉️ for similar stories like this one. Receive the news every day in your inbox. Free of ads. 10 USD per year.
PPC Land explains
Privacy-Enhancing Technologies (PETs): Digital solutions that enable organizations to collect, process, analyze and share information while protecting the confidentiality of personal data. According to the OECD definition, these technologies permit relatively high utility from data while minimizing the need for data collection and processing. PETs represent a fundamental shift from traditional data protection approaches that rely primarily on legal and procedural safeguards.
Data Obfuscation: Techniques that alter data by adding "noise" or removing identifying details to protect individual privacy while maintaining analytical value. This category includes anonymization, pseudonymization, synthetic data generation, and differential privacy. Data obfuscation enables privacy-preserving machine learning and allows information verification without requiring disclosure of sensitive personal information.
Encrypted Data Processing: Advanced cryptographic methods that allow computations to run over data that remain encrypted throughout the process. This includes homomorphic encryption, multi-party computation, and trusted execution environments. These tools represent the most significant advancement in private data processing, eliminating traditional vulnerabilities that occur when data must be decrypted for analysis.
Federated Learning: A distributed approach that enables analytical tasks to be executed on data without requiring the data to leave their original location. Only summary statistics or model parameters are shared rather than raw data. This technique reduces privacy risks by keeping sensitive information at its source while still enabling collaborative analysis and machine learning across multiple organizations.
Cross-Border Data Transfers: The movement of personal data across international boundaries, which faces increasing regulatory scrutiny under various privacy laws. Privacy-enhancing technologies offer potential solutions for enabling compliant international data flows by providing technical safeguards that protect individual privacy while maintaining data utility for legitimate business purposes.
GDPR (General Data Protection Regulation): The European Union's comprehensive data protection law that established the principle of "data protection by design and by default" in Article 25. This regulation requires organizations to implement appropriate technical and organizational measures to ensure privacy protection, making it a key driver for privacy-enhancing technology adoption across multiple industries.
Regulatory Frameworks: The evolving legal structures governing data protection and privacy across different jurisdictions. These frameworks increasingly recognize privacy-enhancing technologies as valid compliance mechanisms, though implementation approaches vary significantly between countries. Harmonization remains challenging due to different legal traditions and policy priorities.
Data Accountability: Systems and processes that manage how data can be gathered, used, and shared while tracking compliance with applicable regulations. These tools control and monitor data access, establish usage rules, and provide immutable records of data processing activities. Though not strictly privacy-enhancing technologies, they enhance privacy through improved governance and control mechanisms.
Anonymization: The process of removing identifying elements from data to prevent re-identification of individuals, theoretically rendering the data outside the scope of privacy regulations. However, the OECD research highlights significant challenges in achieving true anonymization, as researchers continue to successfully re-identify supposedly anonymized datasets through various analytical techniques and auxiliary data sources.
Technical Implementation: The practical deployment of privacy-enhancing technologies within existing organizational systems and workflows. This encompasses the technical architecture, integration challenges, computational overhead, and operational requirements needed to successfully deploy these technologies. Implementation complexity often serves as a significant barrier to adoption, particularly for organizations with limited technical resources or expertise.

