Online identity verification has lagged behind other digital commerce innovations, often requiring users to photograph government-issued IDs and upload selfies—a process that creates friction and exposes personal data to potential theft. WebKit announced on October 3, 2025, that Safari 26 will support the W3C Digital Credentials API, allowing websites to request mobile identity documents directly from digital wallets across iPhone, iPad, and Mac devices.
The announcement from Marcos Cáceres, Erik Melone, and Andreas Thoma detailed how the new API implementation addresses long-standing problems with online identity verification. Current methods require users to locate physical identification documents, photograph them in appropriate lighting conditions, and frequently submit additional selfie verification. These cumbersome processes have led to high abandonment rates during online transactions while requiring businesses to maintain expensive verification systems with limited privacy protections.
Subscribe PPC Land newsletter ✉️ for similar stories like this one. Receive the news every day in your inbox. Free of ads. 10 USD per year.
Mobile documents meet web standards
Mobile identity documents, known as mdocs, represent secure electronic versions of government-issued credentials that can be stored on smartphones. The format adheres to ISO/IEC 18013-5 and ISO/IEC 18013-7 standards, which establish protocols for presenting digital identity documents both in person and online. These standards incorporate several technical safeguards that distinguish mdocs from traditional photo-based verification methods.
Data minimization allows requesting parties to obtain only necessary information for specific transactions. Cryptographic signatures ensure identity data integrity and prevent forgery, reducing identity theft risks during credential presentation. Device binding employs device signatures to prevent ID cloning and replay attacks. Session encryption protects all personally identifiable information exchanged between the mdoc and requesting party, maintaining user data confidentiality throughout the verification process.
Starting with Safari 26 on macOS 26, iOS 26, and iPadOS 26, websites can request mobile IDs from Apple Wallet and third-party wallet providers directly through Safari and other WebKit-based browsers. The implementation follows international standards to ensure interoperability across platforms adopting the same protocols.
Technical implementation across devices
The verification process varies slightly depending on the device but maintains consistent security principles. On Safari for iPhone, a user taps a "Verify Identity" button on a website, which invokes the W3C Digital Credentials API. A system interface appears, allowing selection of a preferred digital identity document, such as a California ID stored in Apple Wallet. A consent sheet then displays the requested information, identifies the website making the request, and indicates whether the site intends to retain the provided data. Information transfers to the website only after the user reviews and authorizes the transaction using biometric authentication or a passcode.
For Mac and iPad users, the process leverages digital identity documents stored on a linked iPhone. After tapping the verification button, users receive a prompt to continue on their nearby iPhone signed into the same Apple account. The consent sheet and authorization steps then proceed identically to the iPhone-only flow. This cross-device functionality maintains security while accommodating users who may be browsing on devices other than their primary smartphone.
Non-Apple platforms can also participate in this verification ecosystem. When a user selects identity verification on these systems, the browser presents a QR code. Opening the iPhone camera app and scanning this code initiates the verification process. The consent sheet appears on the iPhone, displaying requested information and the requesting website's identity. Authorization via biometric or passcode completes the transaction, sending encrypted data to the originating website.
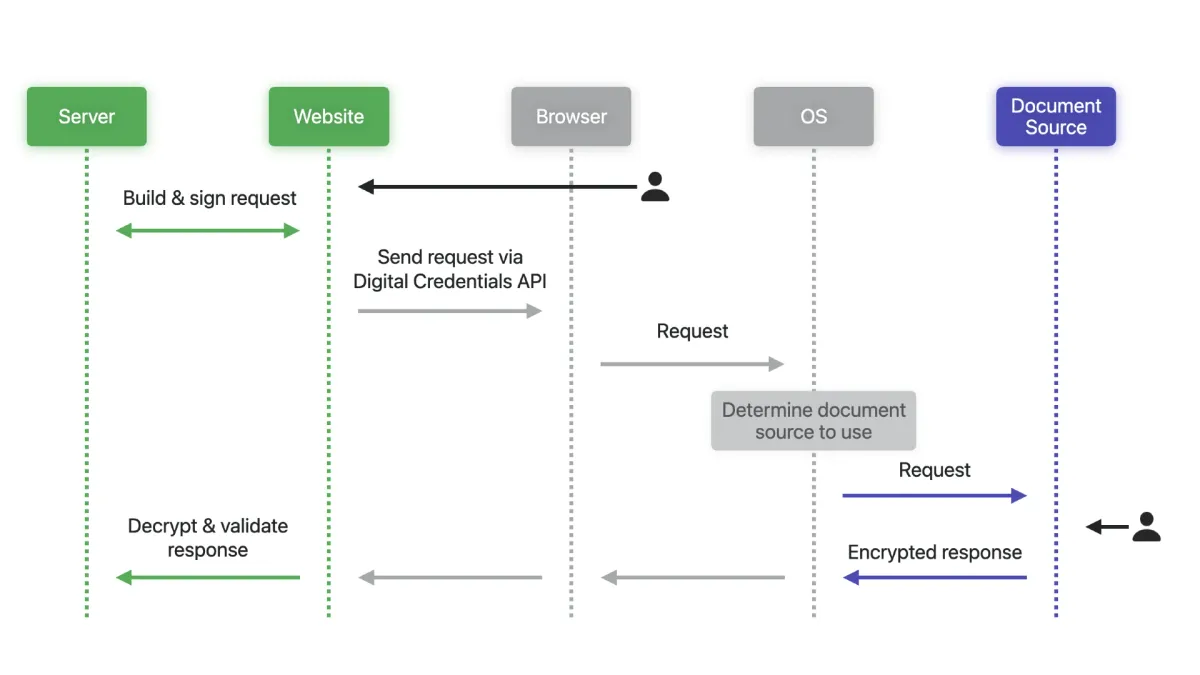
Behind the authentication process
The technical flow begins when a user initiates a credential request through a website action. The website's server creates and cryptographically signs a document request, which the site then submits through the Digital Credentials API via JavaScript. The browser forwards this request to the operating system, which determines available document sources such as Apple Wallet or alternative wallet applications and presents options to the user.
After the user selects a wallet, that application manages consent and authorization procedures. An encrypted response containing the requested data returns to the website, where the server decrypts and validates the information. This architecture separates presentation from verification, allowing the requesting party to independently confirm the authenticity of received credentials.
The Digital Credentials API follows W3C standards for its JavaScript interface. Request formatting adheres to ISO/IEC 18013-7 Annex C and ISO/IEC 18013-5 specifications. Cross-platform flows utilize the FIDO CTAP protocol, ensuring consistency across different devices and operating systems.
Buy ads on PPC Land. PPC Land has standard and native ad formats via major DSPs and ad platforms like Google Ads. Via an auction CPM, you can reach industry professionals.
Developer integration requirements
Website developers implementing digital identity verification must complete three primary steps. First, building the request requires the website server to create a properly formatted request specifying the document type (such as a driver's license in mdoc format), required data elements (including full name, age, or other fields), and whether the site intends to retain this information. The request must also include encryption parameters—keys and nonces for encrypting and signing the response—and authentication structures containing a signed ReaderAuth structure that helps identify the website to document providers.
Making the API call demands specific JavaScript code structure. The call must be triggered by a user gesture, such as a button click, preventing websites from requesting identity information without explicit user interaction. This security measure operates automatically within the browser. The API returns an encrypted credential that the website must send back to its server for decryption.
Processing the response involves several validation steps. The server decrypts the response using its private key, then validates the issuer's signature through the IssuerAuth structure as defined in ISO/IEC 18013-5. Verification of individual data elements requires computing and comparing hash digests to confirm authenticity. Finally, the server must confirm the document originated from the device to which it was issued by validating the DeviceAuth structure. ISO/IEC 18013-5 defines the precise procedures for these validation steps.
Security architecture and verification layers
The mdoc format includes multiple protection layers designed to detect, deter, and mitigate security risks. Request authentication requires websites to identify themselves using certificates, ensuring users understand exactly which entity is requesting their information. End-to-end encryption protects responses using keys generated by the requesting website, preventing unauthorized parties from accessing transmitted data.
Issuer authentication employs digital signatures that prove identity data authenticity and prevent tampering. Device binding uses device signatures to protect against ID cloning and replay attacks. These security measures operate independently but complement each other, creating a defense-in-depth approach to identity verification.
Application developers building identity document provider apps can integrate with Identity Document Services, a framework enabling document presentation on devices and supporting web browser integration with the Digital Credentials API. After authorization, users can select these apps during identity document requests, where developers control the presentation interface. Developers must register with Apple Business Connect to receive certificates for requesting IDs from Apple Wallet, though different document providers may have distinct onboarding requirements.
Market implications and adoption timeline
The technology represents a departure from photo-based verification systems that have dominated online identity checks. California introduced digital driver's licenses in Apple Wallet in August 2024, joining five other states in implementing similar programs. The infrastructure necessary for widespread adoption continues to expand as multiple jurisdictions issue mobile driver's licenses and state IDs.
For marketing technology platforms, standardized identity verification could affect targeting capabilities and compliance procedures. Verified user attributes might enable more precise audience segmentation without relying on third-party cookies or probabilistic matching. This aligns with privacy-focused advertising strategies that prioritize user consent and data minimization.
The mdoc standard's data minimization principle allows websites to request only necessary information for specific transactions. A car rental service verifying age eligibility need not access a customer's full address or organ donor status. This selective disclosure differs from traditional ID verification, where photographed documents expose all printed information regardless of relevance.
Why this matters for marketing
Digital identity verification impacts customer acquisition costs and conversion funnel efficiency. Traditional verification methods introduce friction at critical transaction points, increasing abandonment rates particularly for mobile users. Biometric authorization completes in seconds, potentially improving completion rates for age-restricted purchases, account registrations requiring identity confirmation, and financial services onboarding.
The technology affects platforms managing user-generated content subject to age verification requirements. European age verification regulations implemented in 2025 demonstrate how regulatory frameworks are expanding across jurisdictions. Rather than collecting and storing sensitive identification documents, platforms can verify age attributes through the Digital Credentials API without retaining underlying document data. This approach reduces data storage obligations and associated security risks while maintaining compliance with age-gating regulations.
Advertising platforms requiring verified user identities for certain campaign types—such as political advertising or financial services promotions—could streamline advertiser verification processes. Digital advertising fraud remains a persistent challenge, with bot traffic and identity deception costing advertisers billions annually. Cryptographically verified credentials provide stronger assurance of user authenticity compared to traditional methods vulnerable to manipulation.
The shift toward privacy-preserving verification aligns with regulatory trends limiting collection and retention of personal data. Consumer trust research from July 2025 revealed that 59% of consumers express discomfort with their data being used for purposes beyond their control, while 65% remain willing to allow data collection when they maintain control over the process. Marketing organizations implementing verification methods that demonstrate respect for user privacy may differentiate their services in increasingly privacy-conscious markets.
W3C digital identity standards introduced in January 2025 provided the technical foundation for implementations like Safari's Digital Credentials API. The coordination between browser manufacturers, wallet providers, and standards organizations creates interoperable systems where users can maintain consistent privacy expectations across platforms.
Subscribe PPC Land newsletter ✉️ for similar stories like this one. Receive the news every day in your inbox. Free of ads. 10 USD per year.
Timeline
- February 2, 2025: W3C introduces Controlled Identifiers specification for cryptographic verification and secure digital interactions
- July 27, 2025: European Commission announces EU-wide age verification system requiring digital identity credentials for adult content access, scheduled for 2026 implementation
- August 2024: California partners with Apple to introduce digital driver's licenses in Apple Wallet, joining five other states
- October 3, 2025: WebKit announces Digital Credentials API support for Safari 26 across macOS 26, iOS 26, and iPadOS 26
- Safari 26 release (upcoming): Digital Credentials API becomes available for website integration
Subscribe PPC Land newsletter ✉️ for similar stories like this one. Receive the news every day in your inbox. Free of ads. 10 USD per year.
Summary
Who: WebKit (Apple's browser engine team) announced the feature through Marcos Cáceres, Erik Melone, and Andreas Thoma. The technology affects website developers, mobile app developers creating identity document providers, and end users with digital IDs in wallet applications.
What: Safari 26 will support the W3C Digital Credentials API, enabling websites to request mobile identity documents (mdocs) directly from digital wallets. The implementation follows ISO/IEC 18013-5 and 18013-7 standards for secure identity document presentation. The system incorporates data minimization, cryptographic signing, device binding, and end-to-end encryption to protect user privacy while enabling online identity verification.
When: WebKit announced the feature on October 3, 2025. The functionality will become available when Safari 26 launches for macOS 26, iOS 26, and iPadOS 26. No specific release date for Safari 26 was provided in the announcement.
Where: The Digital Credentials API functions across Safari browsers on iPhone, iPad, and Mac devices. The system also supports cross-platform verification using QR codes for non-Apple platforms, with authentication occurring on the user's iPhone. Digital identity documents can originate from Apple Wallet or third-party wallet applications implementing the Identity Document Services framework.
Why: Traditional online identity verification requires photographing physical IDs and often submitting selfies, creating friction that increases abandonment rates while exposing users to identity theft risks. The Digital Credentials API addresses these problems by enabling cryptographically secured, privacy-preserving verification that transmits only requested data elements. This approach reduces verification costs for businesses, minimizes user data exposure, and streamlines authentication flows across web and mobile environments.

